In the ever-evolving landscape of cybersecurity threats, a chilling new method has emerged that poses a significant risk to data security and user privacy. Researchers from prominent British universities have uncovered a groundbreaking hack that utilizes keystrokes’ voices, exploiting the power of deep learning to steal sensitive information.
This method showcases the alarming potential of modern technology to breach even the most robust security measures.
Your mic puts you at risk of hacks with 95% accuracy
In a groundbreaking study reported by Bleeping Computer, a team of researchers hailing from British universities has unveiled a startling new threat: acoustic hack. By harnessing the capabilities of deep learning models, these researchers have demonstrated the ability to steal data from keyboard keystrokes recorded through a microphone with an astounding accuracy of 95%. This technique represents a concerning advancement in cyberattacks, showcasing the ever-growing sophistication of hacking methods.

Interestingly, when the researchers utilized Zoom for training their sound classification algorithm, the prediction accuracy only dipped slightly to 93%. While still alarmingly high, this lower accuracy on Zoom demonstrates the versatility and potency of this attack method across various communication platforms. This finding underscores the need for heightened awareness and vigilance regarding data security, particularly in the era of remote work and virtual meetings.
How does it work?
The attack begins by recording the victim’s keystrokes so that a prediction algorithm can be trained. This may be done with the use of a nearby microphone or by using malware that gains access to the microphone on the target’s phone.
Another method involves secretly capturing the target’s keystrokes during a Zoom conversation and then cross-referencing those with the target’s voicemails to deduce what the target was saying.
The researchers recorded the sounds made by tapping each of 36 keys on a new MacBook Pro 25 times to use as training data.
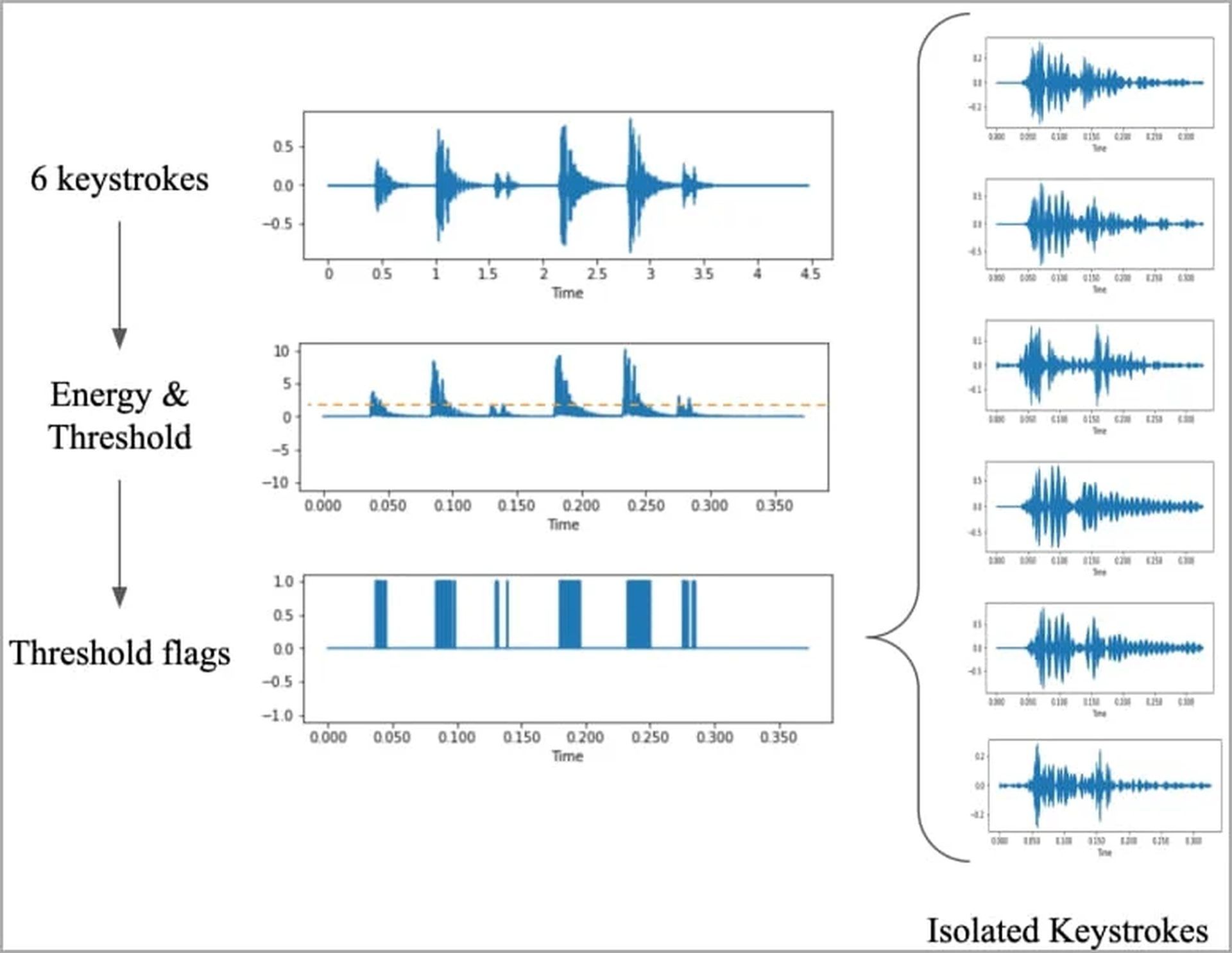
The recordings were then processed in a certain way to enhance the signals that may be utilized for detecting keystrokes, and the resulting waveforms and spectrograms were used to depict the distinguishable changes between each key visually.
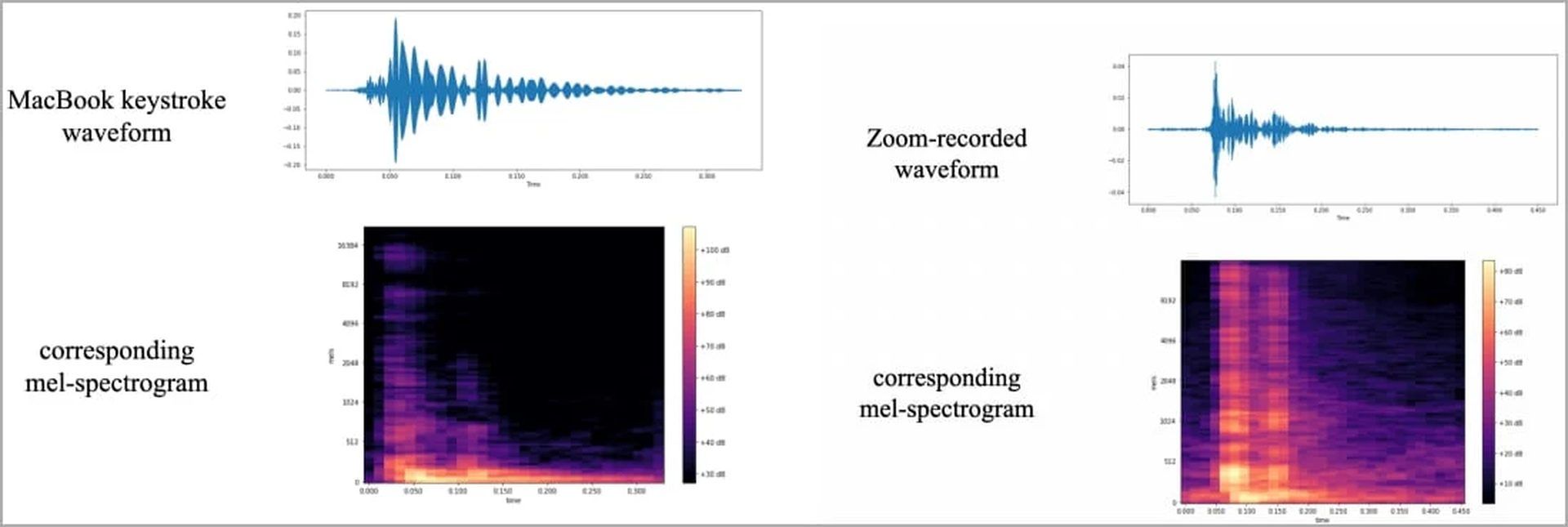
Training the image classifier ‘CoAtNet,’ using spectrogram images, took some trial and error with epoch, learning rate, and data splitting parameters to find the sweet spot that yielded the highest prediction accuracy.
The researchers conducted their tests with an iPhone 13 mini situated 17cm away from the target, Zoom, and the identical laptop whose keyboard has been used in all Apple computers for the previous two years.
The smartphone recordings gave the CoANet classifier an accuracy of 95%, while the Zoom recordings gave it an accuracy of 93%. Skype’s results were less impressive but still useable, at 91.7%.
For detailed information, click here.
Is a new hack trend starting?
What sets the keystrokes voices hack apart from other cyber threats is its reliance on acoustic attacks. Unlike traditional side-channel attacks that often require specific conditions and are subject to data rate and distance limitations, acoustic attacks have become increasingly simple due to the widespread availability of microphone-bearing devices capable of capturing high-quality audio. This accessibility, combined with the rapid advancements in machine learning, has significantly elevated the potential of sound-based side-channel attacks, rendering them far more dangerous than previously anticipated.
This novel attack method strikes at the heart of data security, potentially compromising sensitive information that users may assume is protected. The keystrokes voices hack has the capability to leak passwords, discussions, messages, and other confidential data to malicious third parties, opening the door to a plethora of privacy breaches and security compromises.
The urgent call for vigilance
As technology continues to evolve at an unprecedented pace, it is imperative that individuals, organizations, and technology providers remain vigilant in safeguarding against emerging cyber threats. The keystrokes voices hack serves as a poignant reminder that innovation in the digital realm cuts both ways – it can empower us but also expose us to unprecedented risks.
To defend against such attacks, stringent measures must be put in place. These include regular software updates, employing robust encryption methods, and implementing multi-factor authentication. However, the only way to prevent these kinds of future acoustic hacks is not to talk to anyone with a mic online.

Furthermore, awareness campaigns and cybersecurity training can empower individuals to recognize and respond effectively to potential threats.
Conclusion
The discovery of the keystrokes voices hack by British researchers shines a spotlight on the ever-evolving nature of cybersecurity threats. This method’s ability to extract sensitive data using sound-based side-channel attacks serves as a stark reminder of the importance of staying ahead of cybercriminals by adopting proactive measures to secure our digital lives.
As technology continues to advance, the battle for data security intensifies, requiring collaborative efforts from individuals, organizations, and the cybersecurity community as a whole. Only through vigilance, education, and innovation can we hope to safeguard our digital landscape from these emerging threats.
Featured image credit: Dries Augustyns/Unsplash






