MIT researchers utilized reverse engineering on-chip interface to investigate the viability of a side-channel attack. According to them, bad actors who want to steal sensitive data from programs running on the computer can take advantage of a processor component that connects several areas of the chip.
Bad actors can launch a side-channel attack to steal sensitive data
The cores, or several computational units, found in contemporary computer processors, share the same hardware resources. The element that makes it possible for these cores to communicate with one another is the on-chip interconnect. However, there is a potential that concurrently running programs on several cores could cause one another to lag if they use the interconnect to transport data across the chip at the same time.
A malicious agent could launch a “side-channel attack” by tracking and measuring these delays to decipher private data stored in software, like a password or cryptographic key.
Based on their findings, researchers developed an analytical model of the traffic flow between CPU cores, which they then used to create and execute remarkably successful side-channel attacks. Then they created two mitigating techniques that let users increase security without altering the computer chip.
“A lot of current side-channel defenses are ad hoc — we see a little bit of leakage here, and we patch it. We hope our approach with this analytical model pushes more systematic and robust defenses that eliminate whole classes of attacks at the same time,” explained the co-lead author, Miles Dai.
Dai co-authored the paper with senior author Mengjia Yan, an assistant professor of electrical engineering and computer science (EECS) and a member of the Computer Science and Artificial Intelligence Laboratory, as well as co-lead author Riccardo Paccagnella, a graduate student at the University of Illinois at Urbana-Champaign, Miguel Gomez-Garcia, John McCalpin, a research scientist at Texas Advanced Computing Center (CSAIL). The study is presented at the USENIX Security Conference.
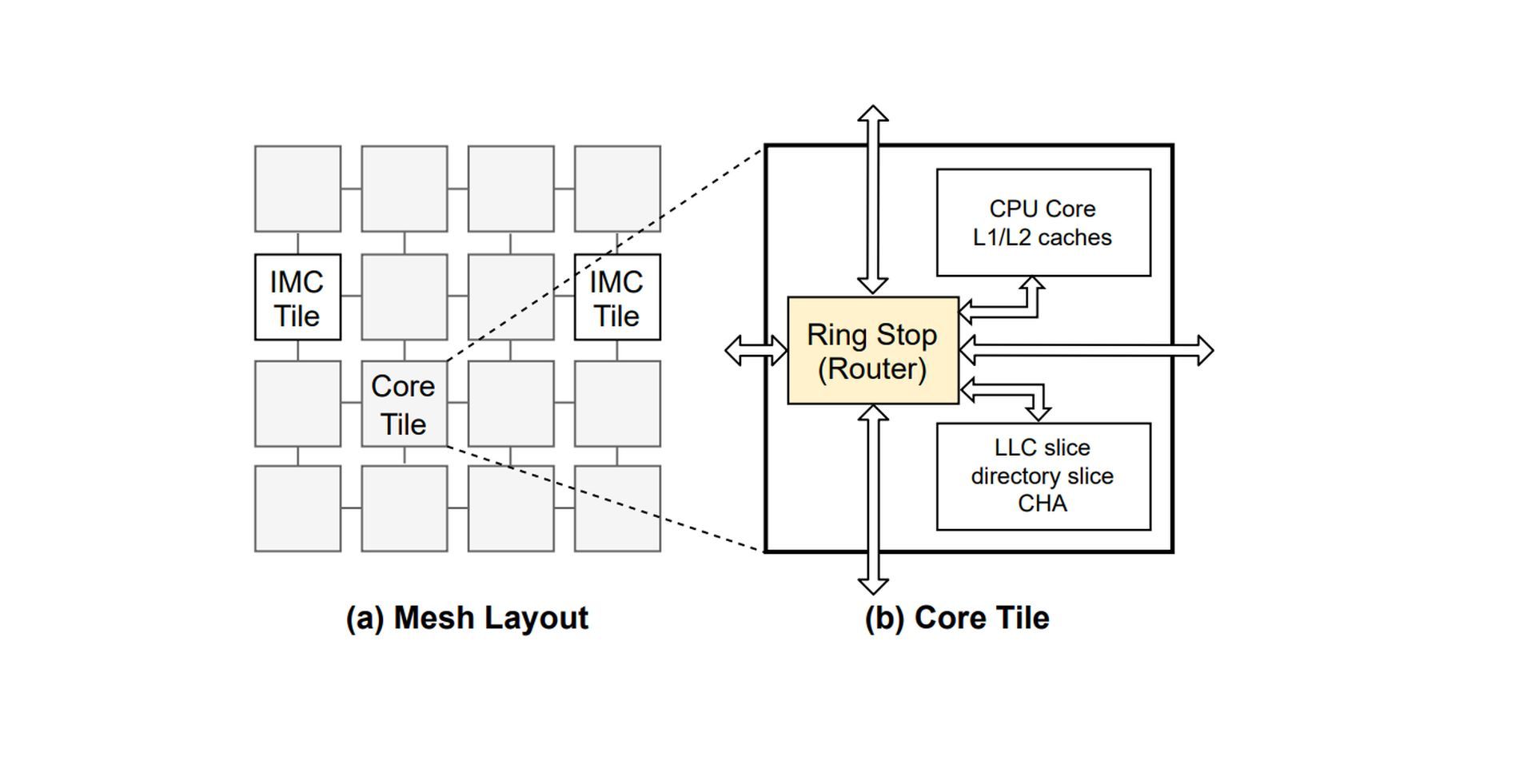
Modern processors have numerous cores arranged in rows and columns, similar to a two-dimensional grid. In addition to a bigger cache shared by the entire CPU, each core has a dedicated cache where data are kept. The on-chip interconnect must be used to send and receive requests for data when a program running on one core needs to access information in a cache on another core or in the shared cache.
According to Dai, despite being a significant portion of the processor, the on-chip interface is still poorly understood since it is hard to hack. Because traffic spends so little time in the interconnect, it is challenging to time the side-channel attack when traffic from two cores truly interferes. There are numerous paths that traffic between cores can follow on the interconnect, which is likewise complicated.
Security as a service leaves cybersecurity to the experts, but it is a double-edged sword
The MIT researchers developed programs that would purposefully access memory caches outside their local cores to analyze how traffic flows across the interconnect.
“By testing out different situations, trying different placements, and swapping out locations of these programs on the processor, we can understand the rules behind traffic flows on the interconnect,” explained Dai.
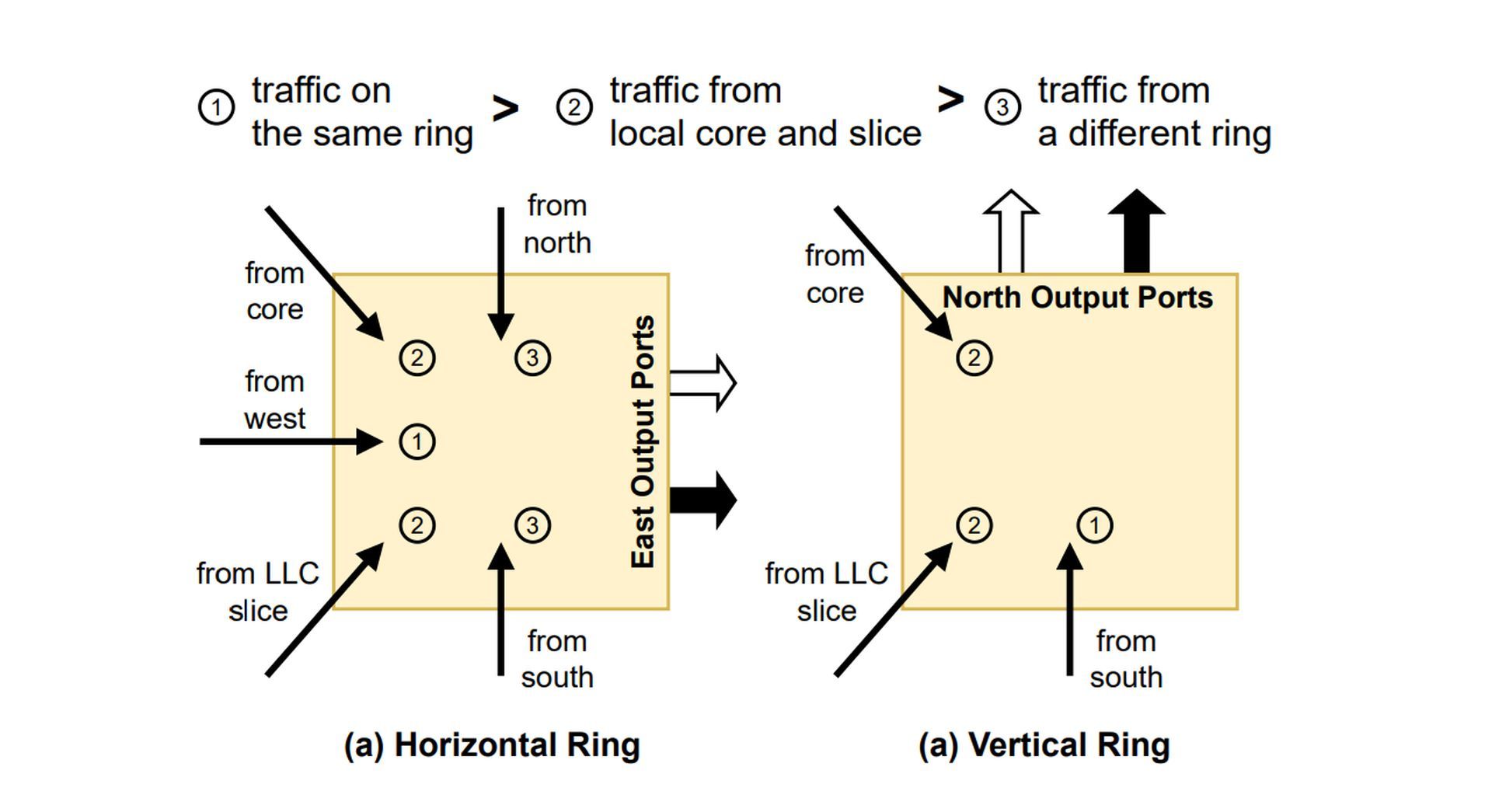
They found that the connection had several lanes traveling in either direction, much like a freeway. The connection uses a priority arbitration policy to determine which traffic flow gets to proceed when two traffic flows conflict. Priority is given to more “important” requests, such as those from applications that are essential to a computer’s functionality.
The researchers used this data to construct an analytical model of the CPU that outlines the possible traffic patterns on the connection. The model identifies the cores that are most susceptible to side-channel attacks. If numerous pathways can reach a core, it becomes more vulnerable. Using this knowledge, an attacker could decide which core to watch closely to steal data from a target program.
Rising cybersecurity risks threaten the healthcare industry
“If the attacker understands how the interconnect works, they can set themselves up so the execution of some sensitive code would be observable through interconnecting contention. Then they can extract, bit by bit, some secret information, like a cryptographic key,” stated Paccagnella.
“On-chip interconnect remains an overlooked attack surface”
The researchers were shocked by how rapidly the side-channel attacks operated after using this model to launch them. From two independent victim programs, they were able to retrieve complete cryptographic keys.
After researching these side-channel attacks, they created two mitigation methods using their analytical model.
The system administrator would implement the first technique by using the model to determine which cores are most susceptible to assaults and scheduling sensitive software to run on those cores. The administrator could set aside cores near a vulnerable program and only execute trusted software on those cores as part of the second mitigating technique.
The researchers discovered that both mitigation techniques effectively lowered side-channel assaults’ accuracy. According to Dai, neither of the mitigations calls for the user to alter the actual hardware, making them rather simple to put into practice.
Finally, they hope their work motivates further researchers to investigate the security of on-chip interconnects, according to Paccagnella.
MIT researchers have built a new LEGO-like AI chip
“We hope this work highlights how the on-chip interconnect, which is such a large component of computer processors, remains an overlooked attack surface. In the future, as we build systems that have stronger isolation properties, we should not ignore the interconnect,” said Paccagnella.





