Oracle has denied a breach of its Oracle Cloud federated SSO login servers and the theft of account data for six million users. However, BleepingComputer has verified multiple companies confirm the validity of the alleged breached data samples.
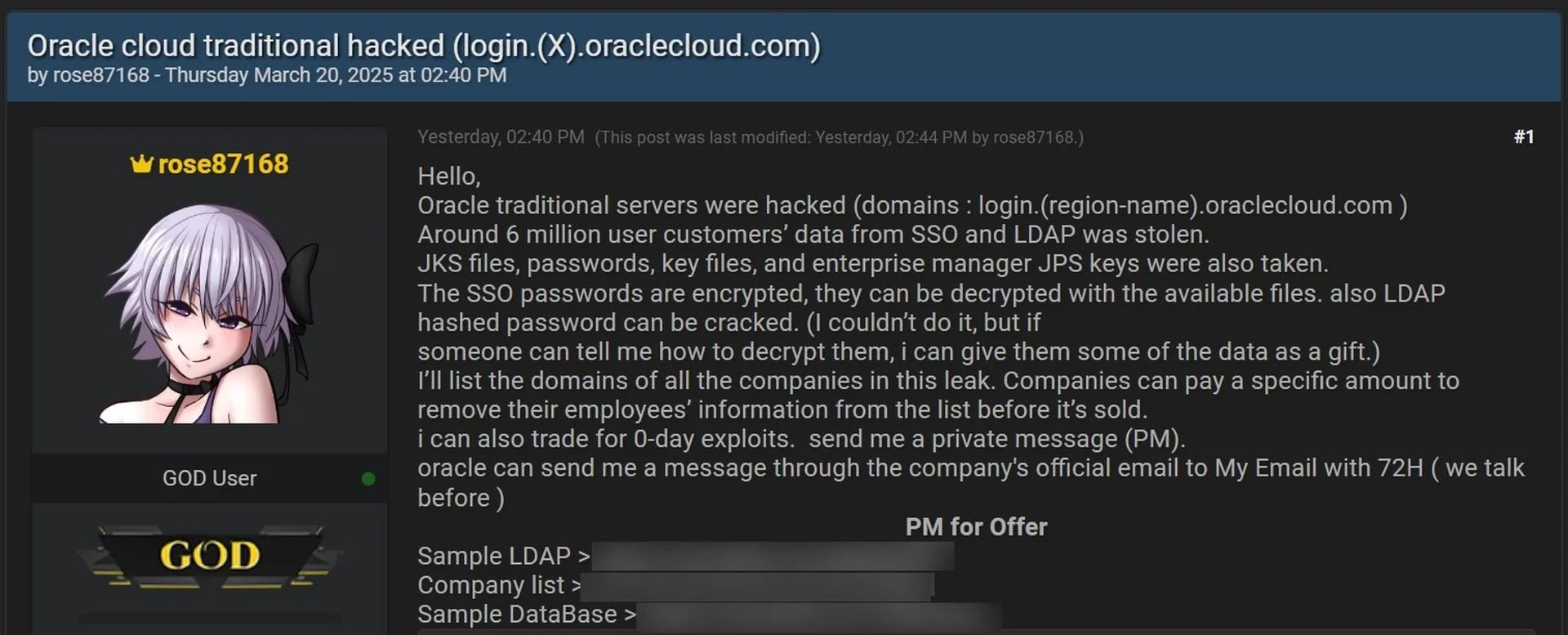
The breach was first reported by a person named rose87168, who claimed to have accessed Oracle Cloud servers. The threat actor began selling alleged authentication data for 6 million users, claiming stolen SSO, and LDAP passwords could be decrypted.
The compromised data includes email addresses, LDAP data, and a list of 140,621 domains for companies and government agencies affected by the breach. However, many of these domains look like tests and multiple domains belong to some companies.
Some domains appear to be tests, and multiple domains exist per company.
rose87168 also provided an Archive.org URL leading to a text file they placed on the “login.us2.oraclecloud.com” server. This demonstrated the hacker’s ability to create files on Oracle’s servers, which supports the likelihood of a breach.
Oracle, however, has refuted the claims of a breach despite the demo of data verification by several companies.
Some listed firms have verified the authenticity of part of the data, including LDAP display names and email addresses, confirming that the breached data is valid.
One of the emails obtained by BleepingComputer demonstrates the threat actor contacting Oracle’s security team about their data. This correspondence shows they reached the intended targeting.
The hacker had contacted Oracle security email claiming to have obtained Oracle Cloud account data for six million users.
BleepingComputer also received communication leading them to believe Oracle was engaged with the threat actor further. This might suggest an attempt at an interaction, but not explicitly pointed out in the source.
The cybersecurity firm Cloudsek discovered that the Oracle Fusion Middleware 11g server was running an older vulnerable version. The threat actor claimed to have exploited a vulnerability in Oracle’s software, tracked as CVE-2021-35587. Ordinarily, this from the archive.org URL, software vulnerabilities can expose bugs and threat factors.
The “login.us2.oraclecloud.com” server was taken offline by Oracle shortly after news of the alleged breach surfaced.
The irony here is that Oracle, the titan of database security, is caught in a denial web that even its own customers are verifying against.
This discrepancy underscores the palpable mystery behind cybersecurity: what constitutes a verifiable breach? That Oracle is taking the server offline—a seemingly ordinary server, but one utilized by defendants—hints at a deliberate yet contradictory response.
It is critical to address the fact that many of these domains are noted as tests, and multiple belong to the same entities, suggesting the attackers either merely scraped directory information or found a way to conjure multiple subdomains in illusionist fashion.
- The cybersecurity firm Cloudsek discovered: An older vulnerable version of Oracle Fusion Middleware 11g running, possibly exploited by CVE-2021-35587.
It is imperative to question the gap between Oracle’s swift action to take down a server and its direct denial of any breach while keeping the loopholes open for further infiltration. This spotlights a growing issue in cybersecurity, where companies must confront the danger presented by outdated software and other vulnerabilities that they have ignored far too long.
The key takeaway is not the denial but the engagement: compartmentalized reports show the threat actor reached Oracle’s security team with stolen data samples. This interaction is telling—Oracle’s defense strategies need comprehensive overhaul, including both beefing up server security and addressing potential vulnerabilities in their software.





