A recent report from Palo Alto Networks’ Unit 42 reveals that macOS users are experiencing a significant rise in infostealer malware attacks, with a 101% increase detected in the last two quarters of 2024.
Rise in infostealer malware attacks targeting macOS users
The report states that these attacks target macOS users across multiple regions and industries. Infostealers are designed to extract sensitive user data from compromised systems. The research identifies three particularly prevalent types of infostealers: Atomic Stealer, Poseidon Stealer, and Cthulhu Stealer.
Infostealers typically utilize the native AppleScript framework, which allows them to manipulate macOS functions and appear as legitimate system prompts, thus deceiving users into revealing their credentials or disabling security measures.
Eric Schwake, director of cybersecurity strategy at Salt Security, emphasized that malware types like Atomic Stealer, Poseidon Stealer, and Cthulhu Stealer highlight the increasing complexity of threats to macOS, urging security teams to maintain vigilance.
Apple recommends that macOS users minimize risk by downloading software exclusively from trusted sources and configuring Privacy & Security settings to control installation sources.
Kaspersky: SparkCat malware is a nightmare for crypto owners
Key infostealer malware types
The Atomic Stealer, known as AMOS, has been available since April 2023. It is marketed as malware-as-a-service on hacker forums and Telegram. This malware can steal a variety of sensitive data, including notes, browser credentials, and cryptocurrency wallet information.
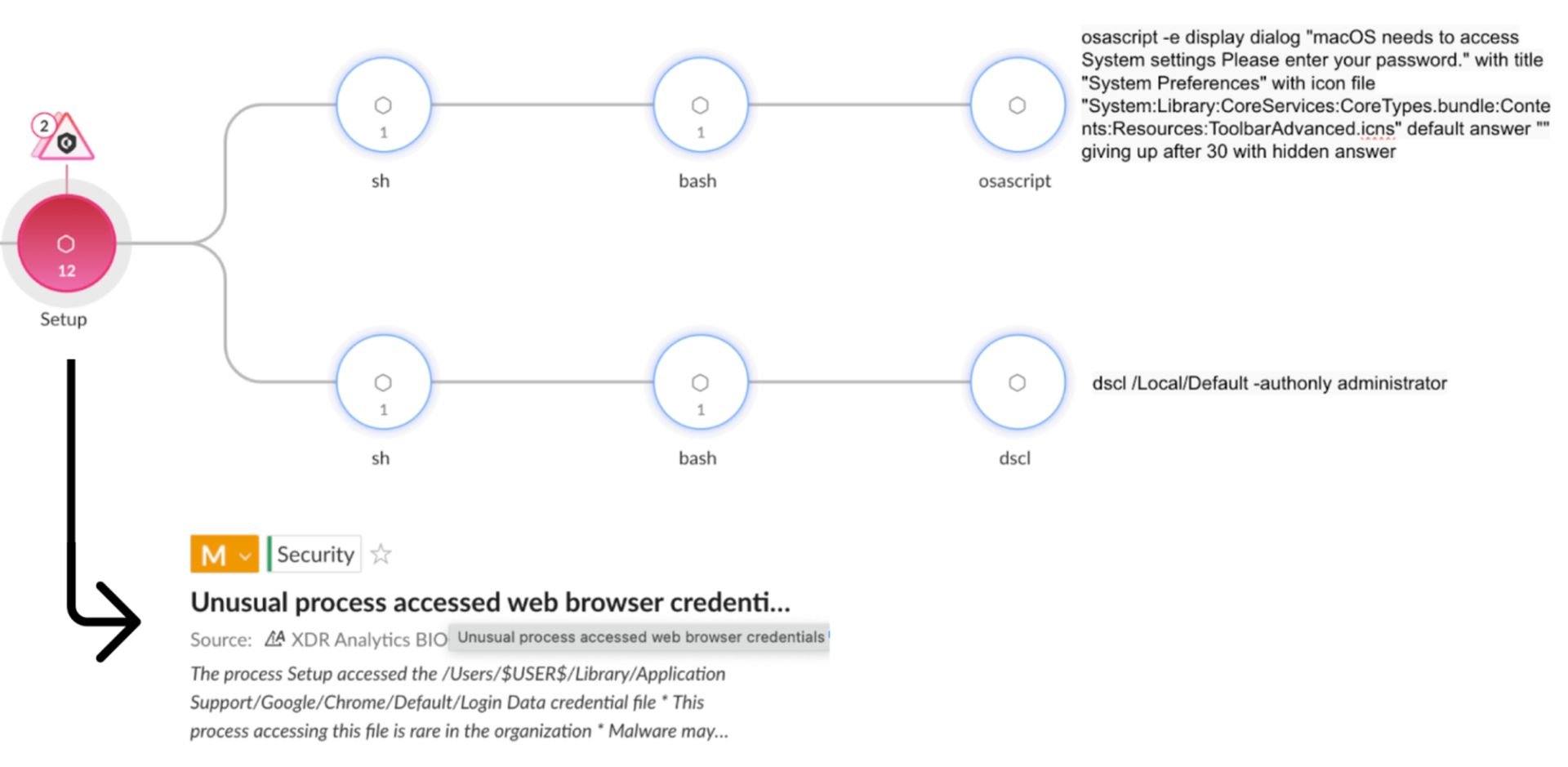
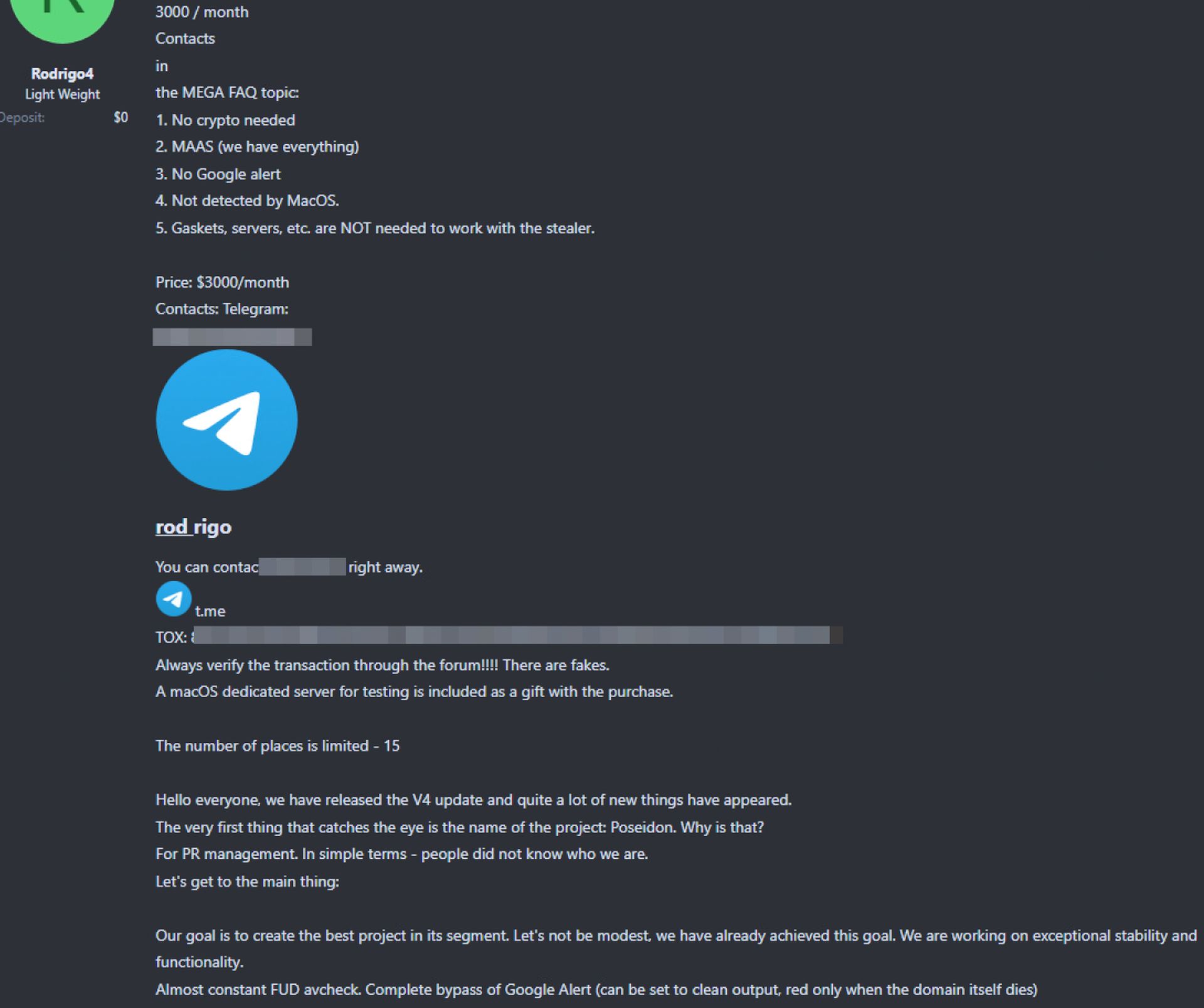
The Poseidon Stealer, advertised by a user known as “Rodrigo4,” has remained active since its sale in August 2024. It infects devices through Trojanized installers that mimic legitimate applications, using encoded AppleScripts to execute its functions, such as stealing browser passwords and collecting user credentials from applications.
Cthulhu Stealer, distributed by operators known as “Cthulhu Team,” is also sold via malware-as-a-service frameworks. Similar to the others, it propagates through malicious installers and seeks a broad range of sensitive information, including browser data, cryptocurrency wallets, and various file types on infected systems.
Palo Alto Networks highlighted that infostealers can lead to severe consequences like data breaches and financial losses. The firm’s telemetry indicates that infostealers represent the largest group of new macOS malware detected in 2024.
To enhance protection, Palo Alto Networks offers advanced detection capabilities through its Cortex XDR and XSIAM platforms, which focus on identifying infostealer threats in macOS environments.
If users suspect their devices have been compromised, they are advised to contact the Unit 42 Incident Response team at their dedicated support numbers across various regions.
Featured image credit: Ales Nesetril/Unsplash





