The BADBOX botnet has now infected over 192,000 Android devices globally, expanding its reach beyond low-cost electronics to include well-known brands like Yandex and Hisense. This malware poses a significant risk as it is pre-installed on devices during manufacturing.
The BADBOX botnet primarily targets Android operating systems and has shown considerable resilience, with the latest telemetry revealing it has affected a wider variety of devices than previously reported. Once activated, infected devices connect to a Command and Control (C2) server, granting attackers access to the local network. The malware can intercept two-factor authentication details and install further malicious software. The infection vector is believed to involve supply chain attacks, where malware is embedded at the firmware level, complicating removal efforts since it resides in a non-writable partition.
Scope of the BADBOX botnet
BitSight suggest that about 160,000 of the infected devices belong to unique models not seen before, affecting high-end products like the Yandex 4K QLED Smart TV and the T963 Hisense Smartphone. The widespread nature of this infection highlights vulnerabilities across various device categories, showing that even trusted brands are not immune.
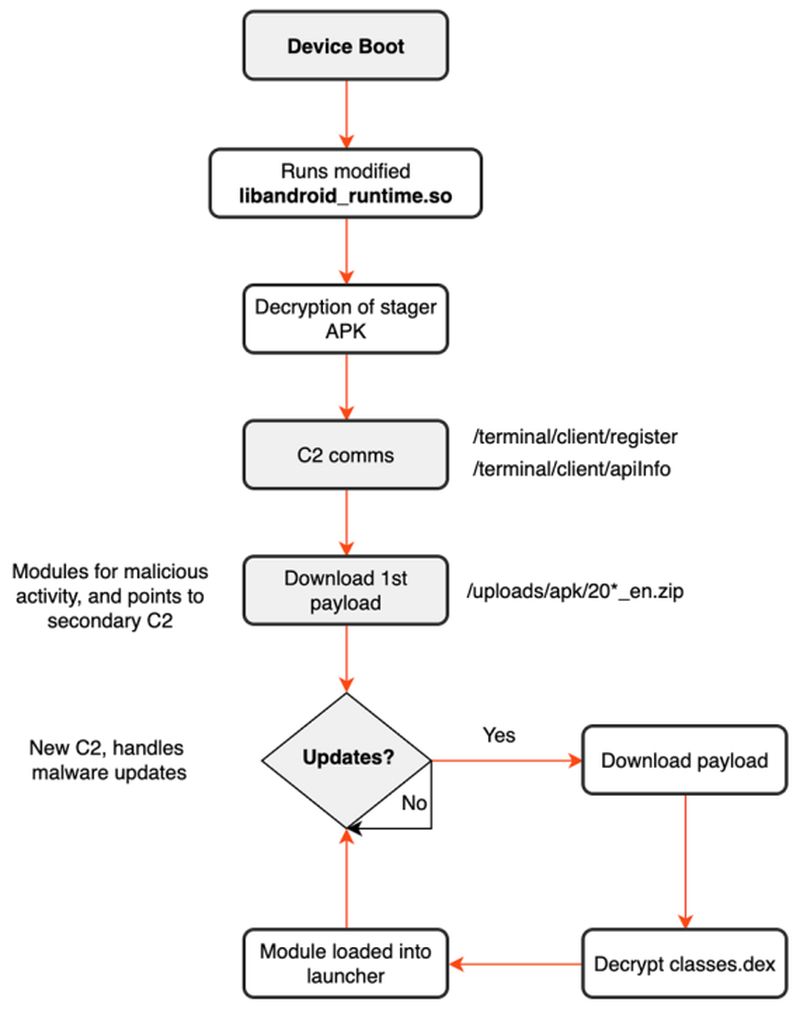
Compromised devices serve multiple malicious purposes. They can act as residential proxies for internet traffic, execute unauthorized remote installations, and even create accounts for spreading misinformation. These activities contribute to a cycle of financial gain for cybercriminals, leveraging infected devices for ad fraud or similar criminal enterprises.
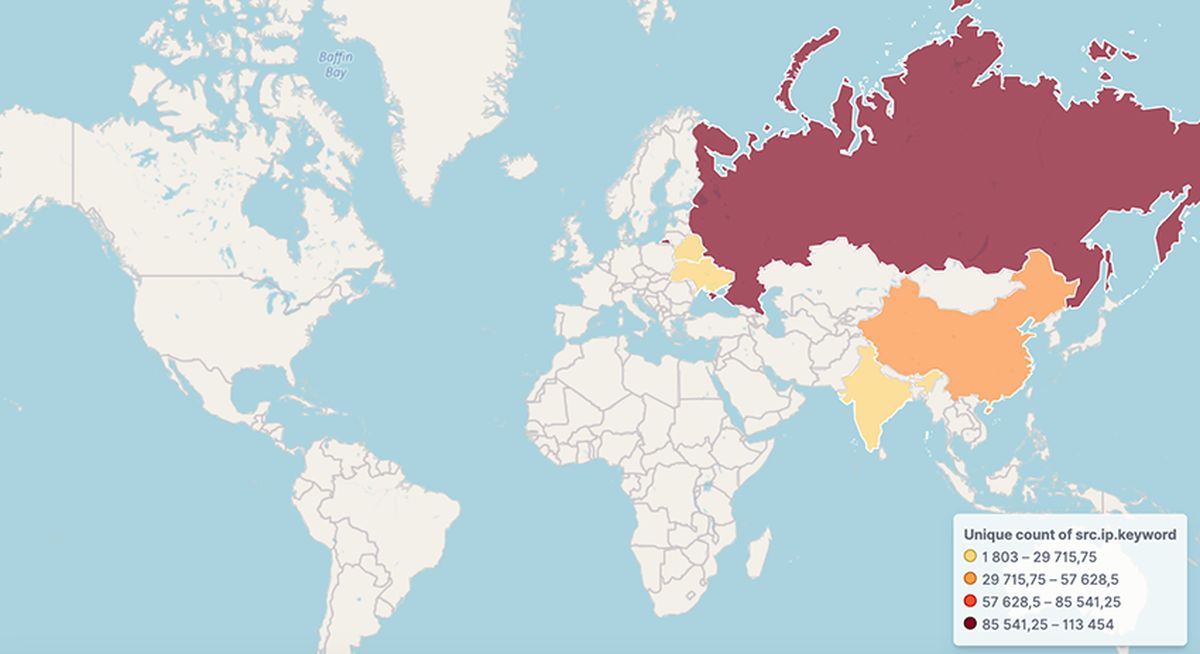
The high incidence of infections spans multiple countries, with significant numbers reported in Russia, China, India, Belarus, Brazil, and Ukraine. German authorities had attempted to disrupt these operations by sinkholing one of the command and control servers, impacting around 30,000 devices primarily composed of Android-based digital picture frames and media streaming boxes. However, this intervention appears to have had limited success, as the overall telemetry of BADBOX shows continued growth and activity.
Russian Secret Blizzard hackers exploit malware to target Ukrainian forces
While efforts to address the issue have been made, including warnings from authorities like Germany’s Federal Office for Information Security (BSI) about the dangers of outdated firmware and pre-installed malware, the challenge remains for manufacturers and retailers. There is a shared responsibility to ensure that devices are secure before they reach consumers.
Consumers need to be particularly vigilant when purchasing devices, especially through popular online platforms such as Amazon, eBay, and AliExpress, where the threat of encountering infected products is heightened. The BSI emphasizes that individuals should ensure their devices receive the latest firmware updates. Additionally, disconnecting devices from the internet when not in use can minimize exposure to ongoing threats.
Another concerning sign of BADBOX infection includes noticeable drops in device performance, overheating, and abnormal network traffic. Expert guidance advises users to be proactive in monitoring these symptoms, which can indicate underlying malware activity that may compromise personal information and device functionality.
Research by cybersecurity company BitSight has amplified understanding of the transmission and persistence of BADBOX, observing over 160,000 unique IP addresses attempting to establish contact with the control domains within just a day. Such growth points to the malware’s ability to adapt and extend its claim across a broader ecosystem of devices.
Featured image credit: Kerem Gülen/Midjourney





