A phishing campaign targeting manufacturing companies in Europe has compromised around 20,000 Microsoft Azure accounts using HubSpot and DocuSign. The operation, which spanned from June to September 2024, primarily affected firms in the automotive, chemical, and industrial sectors in Germany and the UK. Threat actors employed HubSpot’s Free Form Builder to create deceptive forms and lured victims with emails mimicking legitimate services.
Phishing campaign compromises 20,000 Microsoft Azure accounts in Europe
Palo Alto Networks’ Unit 42 identified the campaign and reported that attackers used HubSpot’s online forms as a trap to capture sensitive information. They crafted 17 different forms, designed to mimic legitimate requests for Microsoft Azure credentials. These forms asked victims in poorly worded English if they were “Authorized to view and download sensitive Company Document sent to Your Work Email?” This prompt claimed to facilitate access to critical documents stored in the “Microsoft Secured Cloud.”
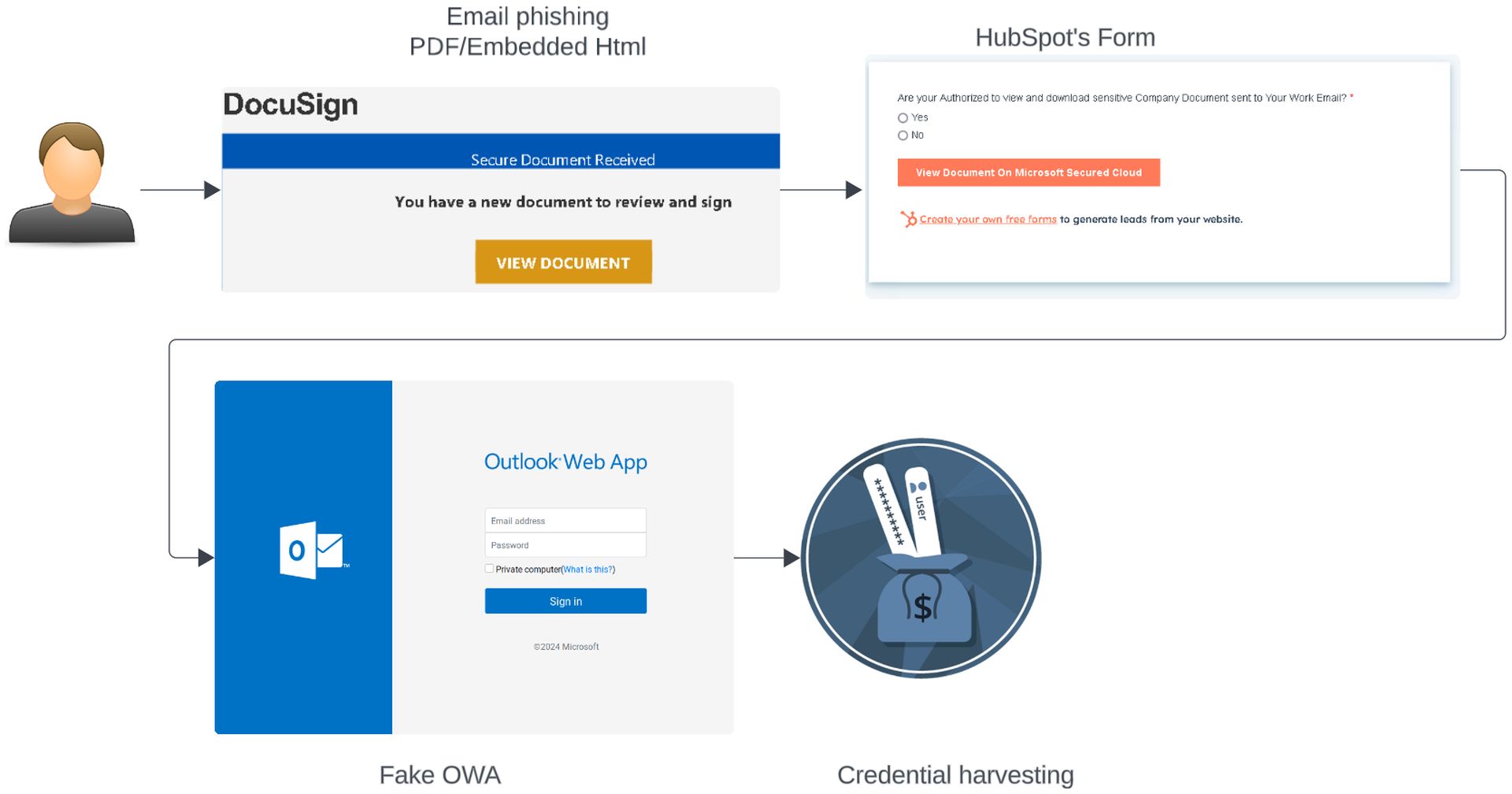
Victims who clicked through the forms were redirected to pages impersonating Microsoft Outlook Web App and Azure login portals, hosted on ‘.buzz’ domains. These tactics allowed attackers to bypass standard email security measures, as the phishing emails linked to a legitimate service (HubSpot). However, the emails did fail SPF, DKIM, and DMARC authentication checks.
Microsoft Teams isn’t safe: Hackers are sneaking in through calls
Once attackers gained access to the compromised accounts, they initiated post-compromise activities. They registered their own devices to victims’ accounts, thus ensuring continued access. Research indicated that threat actors frequently connected through VPNs located in the same countries as their targets, helping them to blend in. In cases where IT teams attempted to regain control of compromised accounts, attackers initiated password resets, creating a tug-of-war scenario that further complicated recovery efforts.
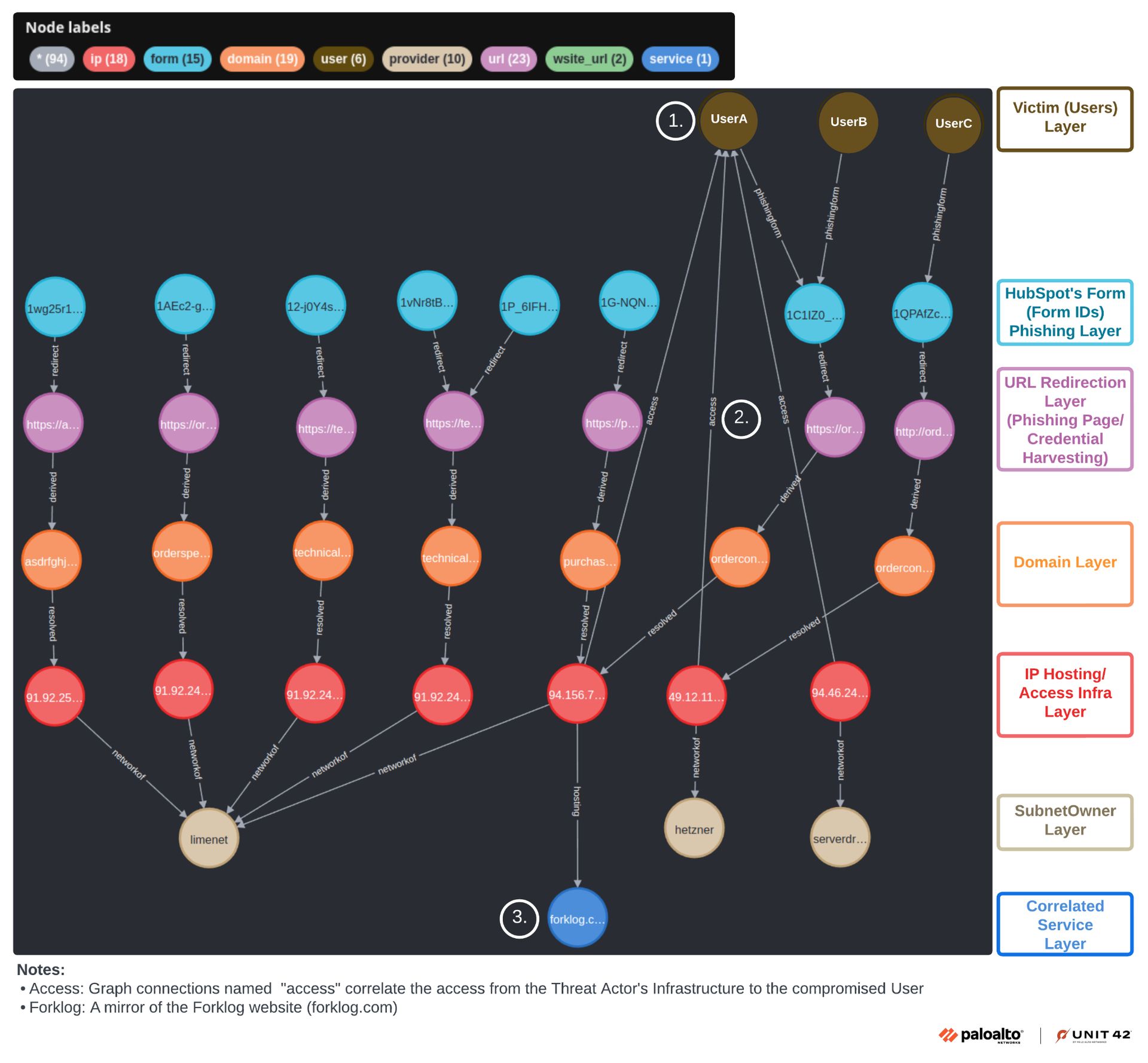
The potential impact of the attacks extends beyond credential theft. With access to Azure accounts, attackers could escalate privileges to create, modify, or delete resources within the compromised cloud environments. They could also potentially move laterally across the network to access sensitive storage containers associated with the victims’ accounts.
While the number of victims who provided Azure credentials is uncertain, security experts suspect it may be lower than the total number of accounts targeted, as not all the victims would have utilized Azure infrastructures. Nathaniel Quist of Unit 42 emphasized that the operation represents a more ambitious shift towards cloud-focused phishing attacks. Increasingly, cybercriminals are targeting user credentials for cloud and SaaS platforms instead of relying on malware to compromise endpoint devices.
Featured image credit: Microsoft





