Cybercriminals are increasingly utilizing Microsoft Teams to execute vishing attacks aimed at accessing users’ systems. Trend Micro reported a specific incident that involved a series of phishing emails followed by a deceptive Microsoft Teams call. The fraudsters pretended to offer tech support and manipulated a victim into downloading remote access software.
Cybercriminals exploit Microsoft Teams for vishing attacks
The attack commenced with a barrage of phishing emails that targeted the victim’s inbox. Shortly after this initial contact, the attacker initiated a call through Microsoft Teams, masquerading as an employee of a company the victim trusted. During this call, the cybercriminal urged the victim to install a remote support application. The initial suggestion was Microsoft Remote Support, but when the installation encountered problems, the attacker pivoted to AnyDesk, a remote desktop tool commonly exploited by malicious actors.
AnyDesk hacked, reset your passwords immediately
Once AnyDesk was installed on the victim’s machine, the attacker gained control over it. They proceeded to deploy various suspicious files, including one identified as Trojan.AutoIt.DARKGATE.D. This malware, delivered via an AutoIt script, enabled the attacker to execute malicious commands and maintain remote control over the system. The attacker executed several commands that gathered detailed information about the victim’s system, employing commands such as systeminfo, route print, and ipconfig /all, which saved the gathered data in a file named 123.txt.
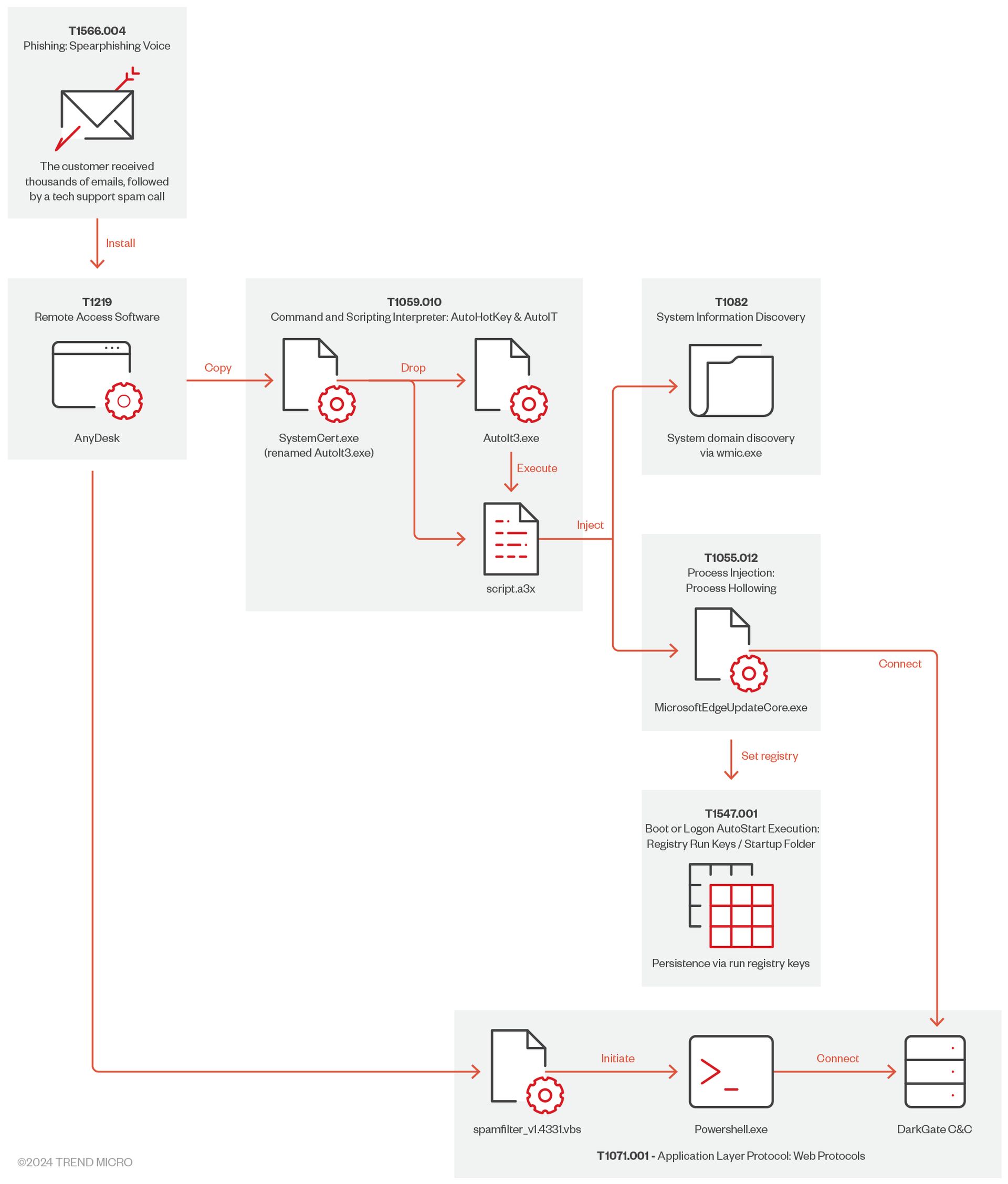
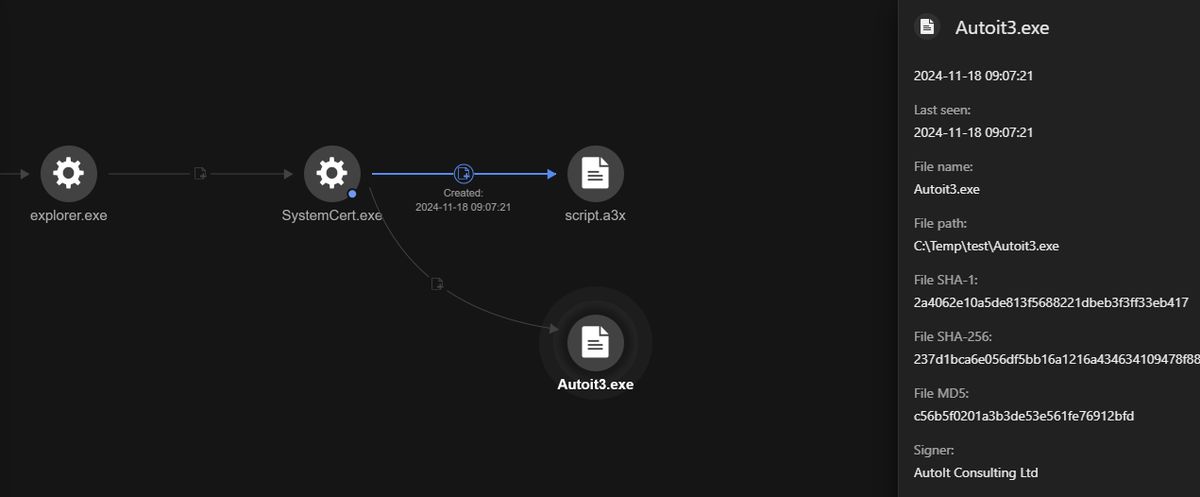
Following the acquisition of access through AnyDesk, the attacker undertook further malicious actions and employed techniques to evade detection. For example, AutoIt scripts were utilized to identify and bypass any antivirus software present on the system. Additionally, malicious files were discreetly downloaded and extracted into hidden directories, thereby reducing the likelihood of detection. Among these was a file named SystemCert.exe, which created additional scripts and executables in temporary folders and facilitated further malicious activities.
Fortunately, the attack was thwarted before any sensitive data was exfiltrated. The investigation revealed that, despite the hackers gaining access and leaving behind persistent files and registry entries, no critical information was stolen from the victim. This incident underscores the urgent need for fortified security measures within organizations to defend against such sophisticated threats.
Best practices to combat vishing attacks
Organizations must adopt comprehensive strategies to mitigate the risks associated with vishing attacks. It is crucial to first verify the claims made by third-party technical support providers. Employees should confirm affiliations before granting any access, which reduces the risk of manipulation by cybercriminals.
Controlling access to remote support tools is another key aspect of a robust security posture. Organizations should consider implementing whitelisting for approved tools like AnyDesk and enforce multi-factor authentication policies for enhanced security. This step adds a necessary layer of protection in preventing unauthorized access.
Employee training is paramount in building awareness around social engineering tactics, including phishing and vishing. Educating staff on recognizing these threats is vital in minimizing their susceptibility to future attacks. Training sessions should focus on the specific techniques used by cybercriminals, as well as practical steps to ensure safety.
Featured image credit: Dimitri Karastelev/Unsplash





