The MeridianLink breach has taken a dramatic turn, showcasing the evolving strategies of cybercriminals in the digital age. The ALPHV/BlackCat ransomware group, known for their sophisticated extortion tactics, has now filed a formal complaint with the U.S. Securities and Exchange Commission. This bold move accuses MeridianLink, a prominent software company, of failing to comply with the strict four-day rule mandated for disclosing cyberattacks.
In a recent development, MeridianLink, known for its digital solutions catering to financial institutions like banks, credit unions, and mortgage lenders, found itself spotlighted on the threat actor’s data leak site.
The stakes are high: the group has issued an ultimatum to MeridianLink, demanding a ransom within 24 hours to prevent the release of the purportedly stolen data. This MeridianLink breach marks a significant escalation in the tactics employed by ransomware operators, showcasing their growing audacity in targeting major, publicly traded companies.
Delving deeper into the MeridianLink breach, we uncover more layers of this cybersecurity crisis. DataBreaches.net reports that ALPHV, also known as BlackCat, claims to have infiltrated MeridianLink’s network on November 7. Their strategy diverged from the typical ransomware playbook: instead of encrypting the company’s systems, they purportedly opted to exfiltrate sensitive data.
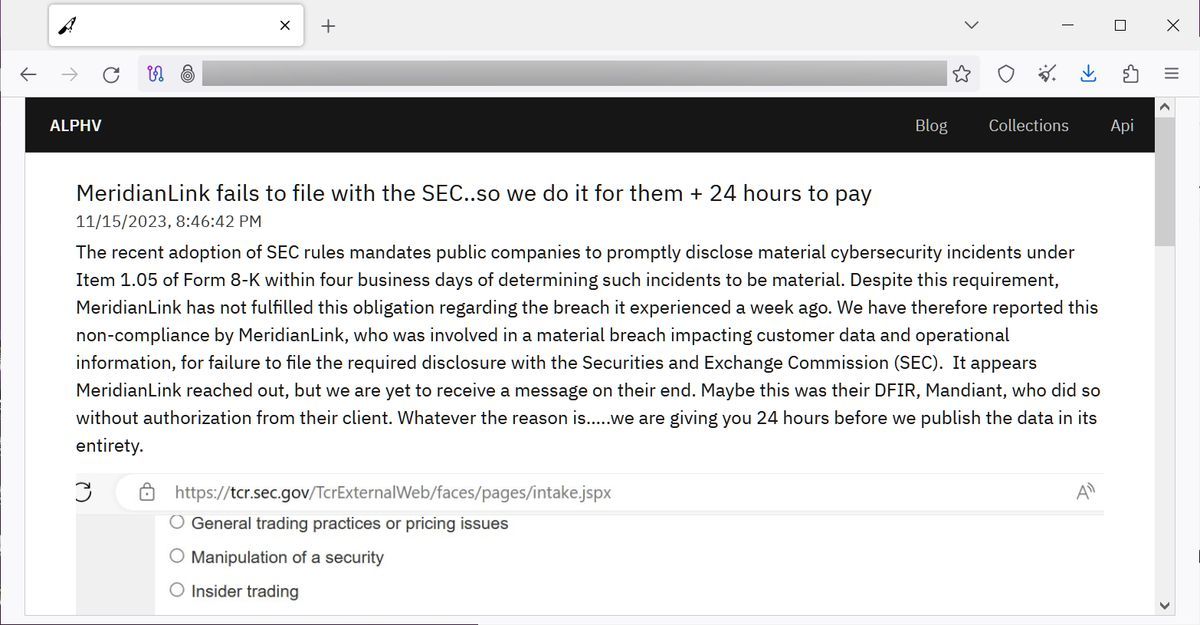
In a twist of events, the ransomware group expressed that while MeridianLink seemingly initiated contact, no substantial communication had occurred regarding a potential ransom for the alleged stolen data. This apparent silence from MeridianLink may have spurred the cybercriminals to adopt a more aggressive stance. They escalated matters by lodging a complaint with the U.S. Securities and Exchange Commission (SEC), accusing MeridianLink of failing to disclose a cybersecurity incident that compromised vital customer data and operational information.
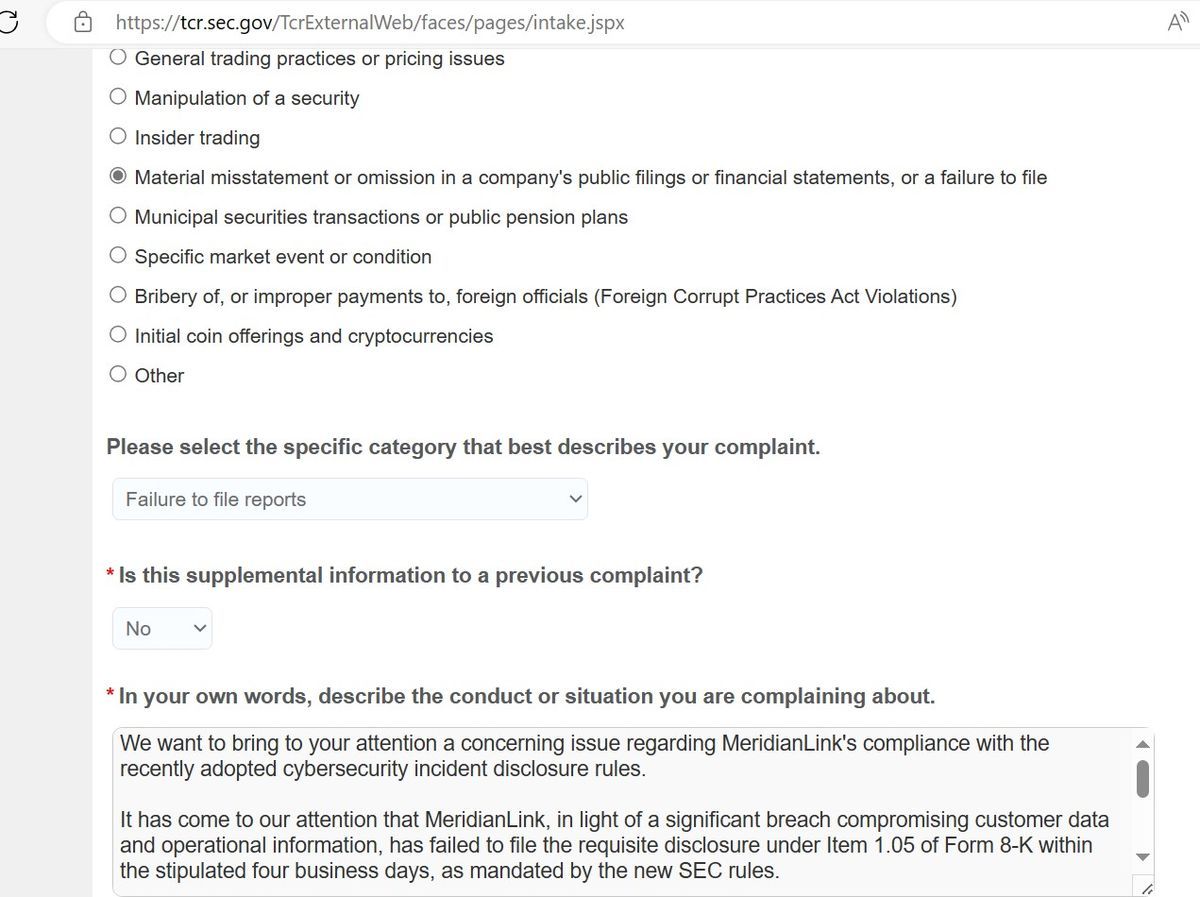
To lend credibility to their claims, ALPHV went as far as to display a screenshot on their website, showcasing the filled-out form on the SEC’s Tips, Complaints, and Referrals page. In their communication to the SEC, the attackers labeled the incident a “significant breach,” alleging MeridianLink’s non-compliance with the disclosure requirements outlined in Form 8-K, under Item 1.05.
Canada data breach exposes government personnel information
This situation echoes a broader context of escalating cybersecurity threats in the U.S. In response to a surge in such incidents like MeridianLink breach, the SEC has implemented new regulations. These rules mandate that publicly traded companies promptly report cyberattacks that could materially influence investment decisions. The MeridianLink breach not only highlights the evolving tactics of ransomware groups but also underscores the critical importance of timely and transparent disclosure.
The new SEC rule stipulates that such incidents must be reported within four business days after a company recognizes the materiality of the breach.
However, there’s a critical timeline to consider. Reuters highlighted in early October that these new SEC cybersecurity rules are slated to become effective on December 15, 2023. This detail adds a layer of complexity to the MeridianLink situation.
Further intensifying the drama, ALPHV has showcased on their site the SEC’s acknowledgment of their complaint against MeridianLink. This move is a clear effort by the ransomware group to prove the legitimacy of their submission and to demonstrate that their actions have tangible repercussions in the regulatory sphere.
MeridianLink breach is officialy confirmed
In a recent development, MeridianLink has acknowledged the cyberattack. Addressing BleepingComputer, the company detailed its immediate response to the incident, highlighting swift actions to contain the threat and the involvement of third-party cybersecurity experts to conduct a thorough investigation.
MeridianLink is currently in the process of assessing whether any consumer personal information was compromised during the cyberattack. The company assures that it will inform affected individuals if any personal data was indeed impacted.
In a reassuring statement, MeridianLink conveyed, “Based on our investigation to date, we have identified no evidence of unauthorized access to our production platforms, and the incident has caused minimal business interruption.”
This scenario marks a significant moment in the landscape of ransomware and extortion tactics. While many cybercriminal groups have previously threatened to report breaches to the SEC, this incident involving MeridianLink may be the first public acknowledgment of such a report actually being made.
Historically, ransomware actors have applied pressure on their victims in various ways, including notifying the victims’ customers about the breach or directly intimidating the victim through phone calls. The move by ALPHV to file a complaint with the SEC represents a novel and more formal escalation in the strategies employed by these cyber extortionists.
Featured image credit: Kerem Gülen/Midjourney