The Federal Risk and Authorization Management Program (FedRAMP) has emerged as a cornerstone for secure cloud adoption within the U.S. federal government. By establishing a standardized approach to security assessment and authorization, FedRAMP empowers agencies to confidently migrate to the cloud, reaping the benefits of increased efficiency, scalability, and cost-effectiveness. This rigorous certification process ensures that cloud service providers (CSPs) meet stringent security requirements, safeguarding sensitive federal data.
For CSPs seeking to serve the federal market, FedRAMP Authorization is a critical milestone. By successfully achieving this certification, CSPs demonstrate their commitment to robust security practices and compliance with government regulations. This, in turn, fosters trust and accelerates the transition to cloud-first strategies within the federal sector.
FedRAMP requirement & challenges:
To achieve FedRAMP authorization, cloud service providers (CSPs) must:
Meet security standards: Implement strong security controls to protect data, such as encryption, access controls, and regular security assessments.
Document security practices: CSPs must document how they implement these security controls and show that they are effective.
Undergo third-party assessment: A third-party organization (3PAO) will review the CSP’s security practices and documentation to ensure they meet FedRAMP requirements.
Maintain continuous compliance: Once authorized, CSPs must maintain their security posture and undergo regular re-assessments to keep their FedRAMP authorization.
In summary, FedRAMP ensures that cloud services used by the federal government are secure and reliable. Further, FedRAMP categorizes cloud service offerings (CSOs) into three impact levels: Low, Moderate, and High. Each level corresponds to increasing levels of security controls and requirements, reflecting the sensitivity of the data processed by the CSO.
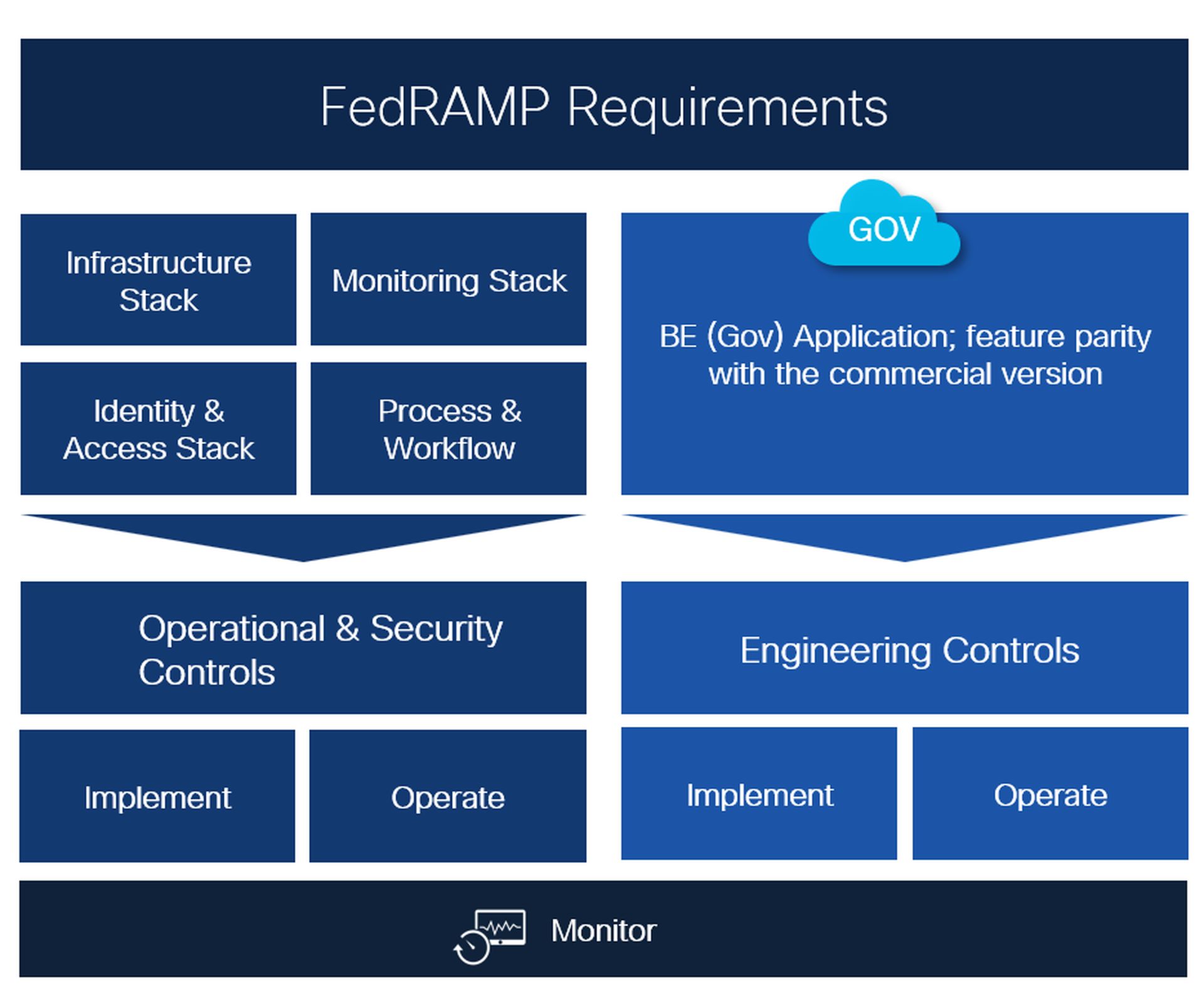
Accelerate the FedRAMP journey using the Driver-Subscriber Approach
The Federal Risk and Authorization Management Program (FedRAMP) presents a significant challenge for organizations seeking to provide software-as-a-service (SaaS) offerings to the U.S. federal government. The rigorous, time-consuming, and costly nature of the FedRAMP authorization process requires organizations to invest substantial resources in both technical and operational aspects. Product teams must not only develop and maintain a government version of their application on a FedRAMP-authorized infrastructure, but they must also ensure feature parity with the commercial version, a requirement often driven by customer expectations rather than explicit FedRAMP mandates. Moreover, these teams must establish a comprehensive security stack, encompassing access management, vulnerability management, configuration management, and identity and access management (IAM), to meet FedRAMP’s stringent security controls. This necessitates additional personnel with deep expertise in FedRAMP compliance and the operational intricacies of maintaining such a security posture.
The FedRAMP Moderate level, for instance, mandates adherence to approximately 325 security controls. To achieve FedRAMP authorization, product teams must not only comply with these core controls but also fulfill various ancillary requirements. This rigorous process can extend the time to FedRAMP audit readiness beyond 24 months. A potential solution lies in the driver-subscriber model, where a common, FedRAMP-authorized platform provides essential security and operational services. By subscribing to this platform, product teams can leverage its pre-existing compliance efforts, streamlining the FedRAMP authorization process and accelerating time-to-market.
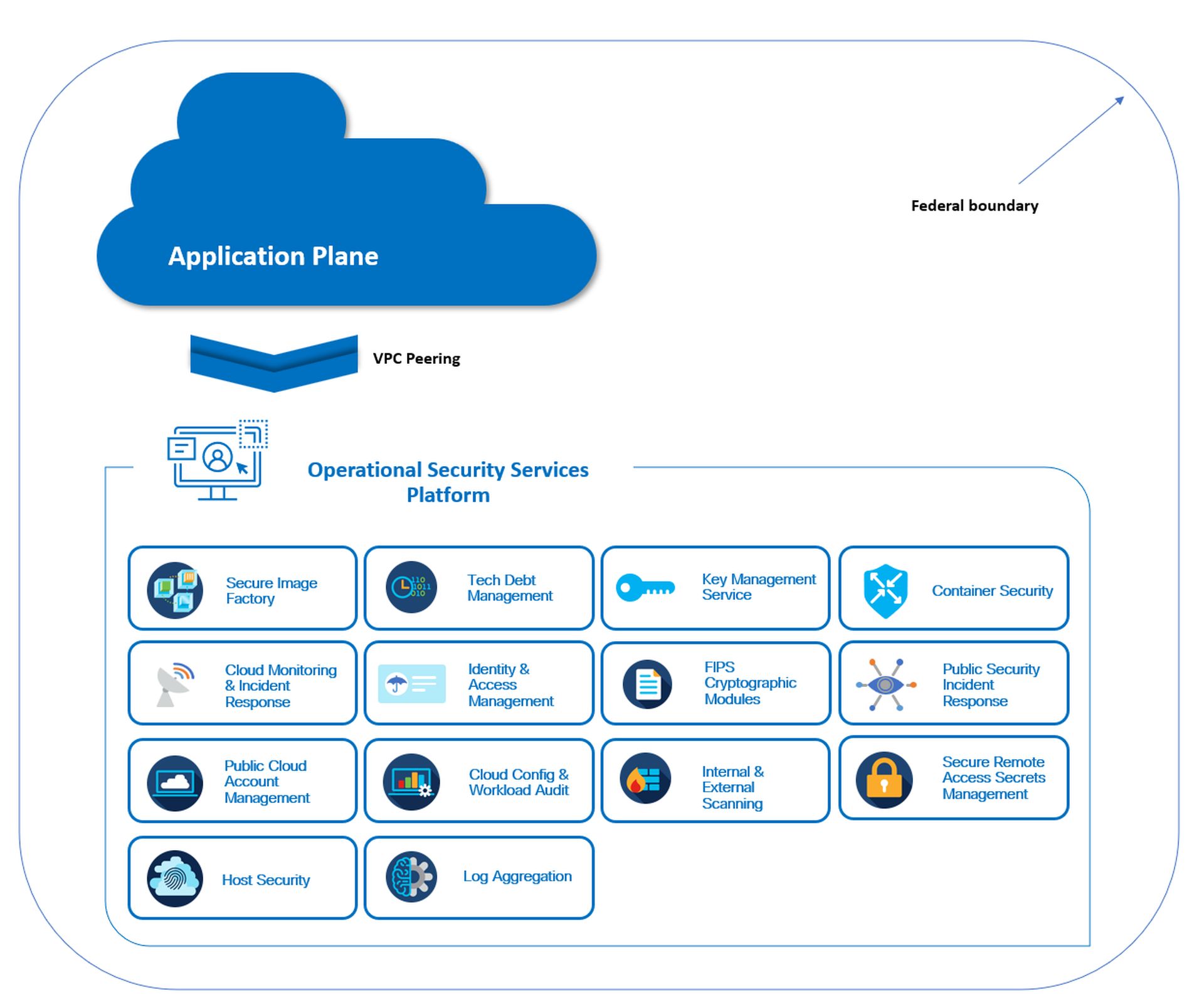
The “driver” platform offers a range of essential security services that can address approximately 40% of the FedRAMP control requirements for product teams. Some critical services include:
- Identity and Access Management (IAM): Provides directory services, single sign-on (SSO), remote access VPN, multi-factor authentication (MFA), and self-service APIs to secure access to applications and data.
- Vulnerability management: Implements vulnerability scanning, attribution, and triaging, container scanning, and dynamic application security testing (DAST) to identify and mitigate security risks.
- Secure Image Factory: Delivers Federal Information Processing Standards (FIPS)-enabled operating system (OS) images, CIS Benchmark-hardened OS configurations, and compliance drift monitoring to ensure secure and compliant infrastructure.
- Security Incident Monitoring: Provides 24/7 Security Operations Center (SOC) services to detect, investigate, and respond to security threats.
By leveraging this driver-subscriber model, product teams can focus on their core competency: developing feature-rich applications. Simultaneously, security teams can concentrate on their expertise: building and managing robust operational security services. This collaborative approach accelerates the process of achieving FedRAMP compliance for product teams.
Featured image credit: Freepik





