According to recent news, someone hacked Discord.io and stole the data of 760k users. The Discord.io data breach has caused a big leak of user data, and the hacker is now selling the information on hacker forums.
A hacker using the alias “Akhirah” triggered a huge data breach against Discord.io. On Monday, August 14, 2023, a data breach occurred that seriously endangered the privacy of almost 760,000 customers’ personal data. Discord.io is a non-official website renowned for offering redirect and invite links to Discord servers.
The database is currently being sold on the updated Breach Forums, which just appeared under the control of the notorious ShinyHunter hackers.
The threat actor said that the information types for 760k users contains are as follows:
"userid","icon","icon_stored","userdiscrim","auth","auth_id","admin","moderator","email","name","username","password","tokens","tokens_free","faucet_timer","faucet_streak","address","date","api","favorites","ads","active","banned","public","domain","media","splash_opt","splash","auth_key","last_payment","expiration"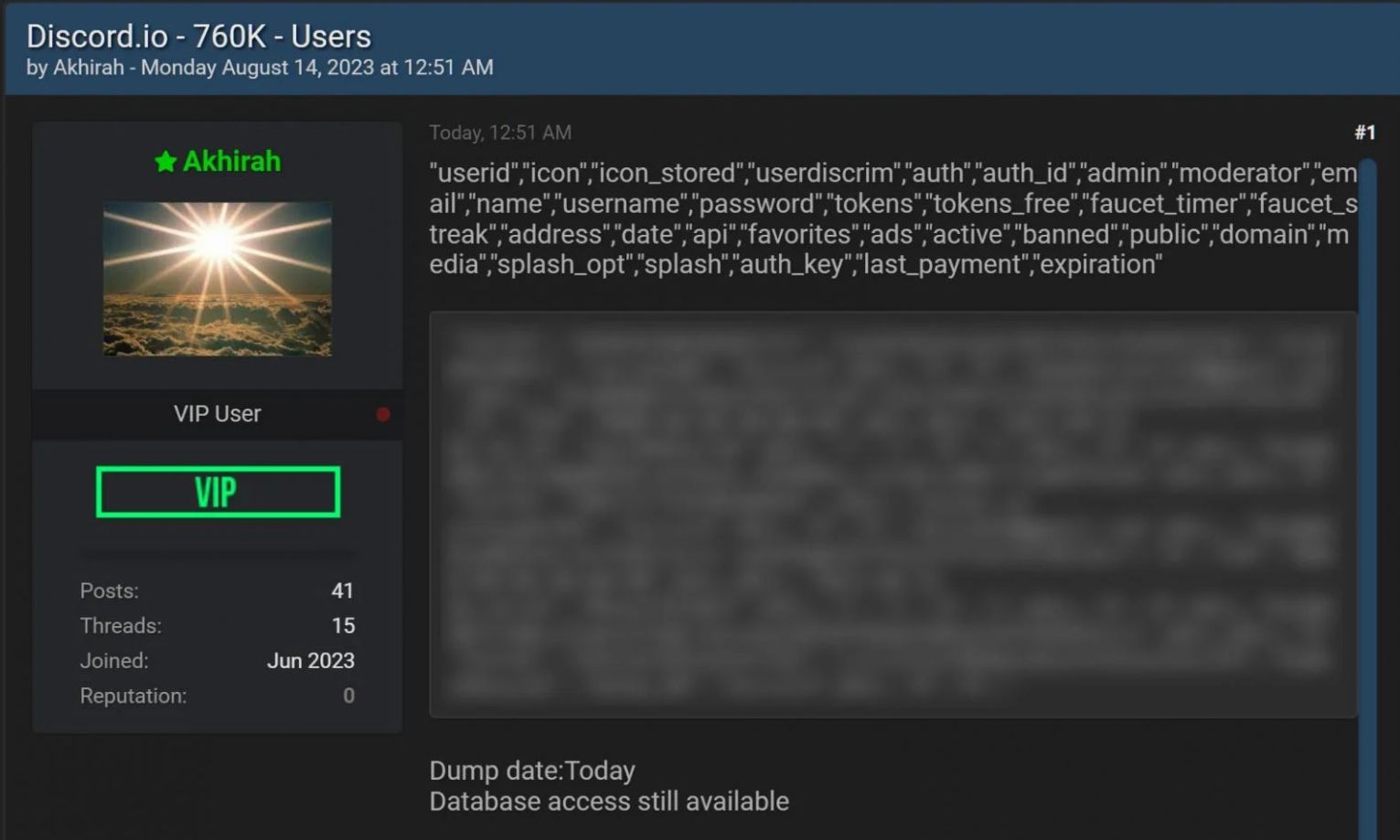
Discord.io data breach confirmed by the website
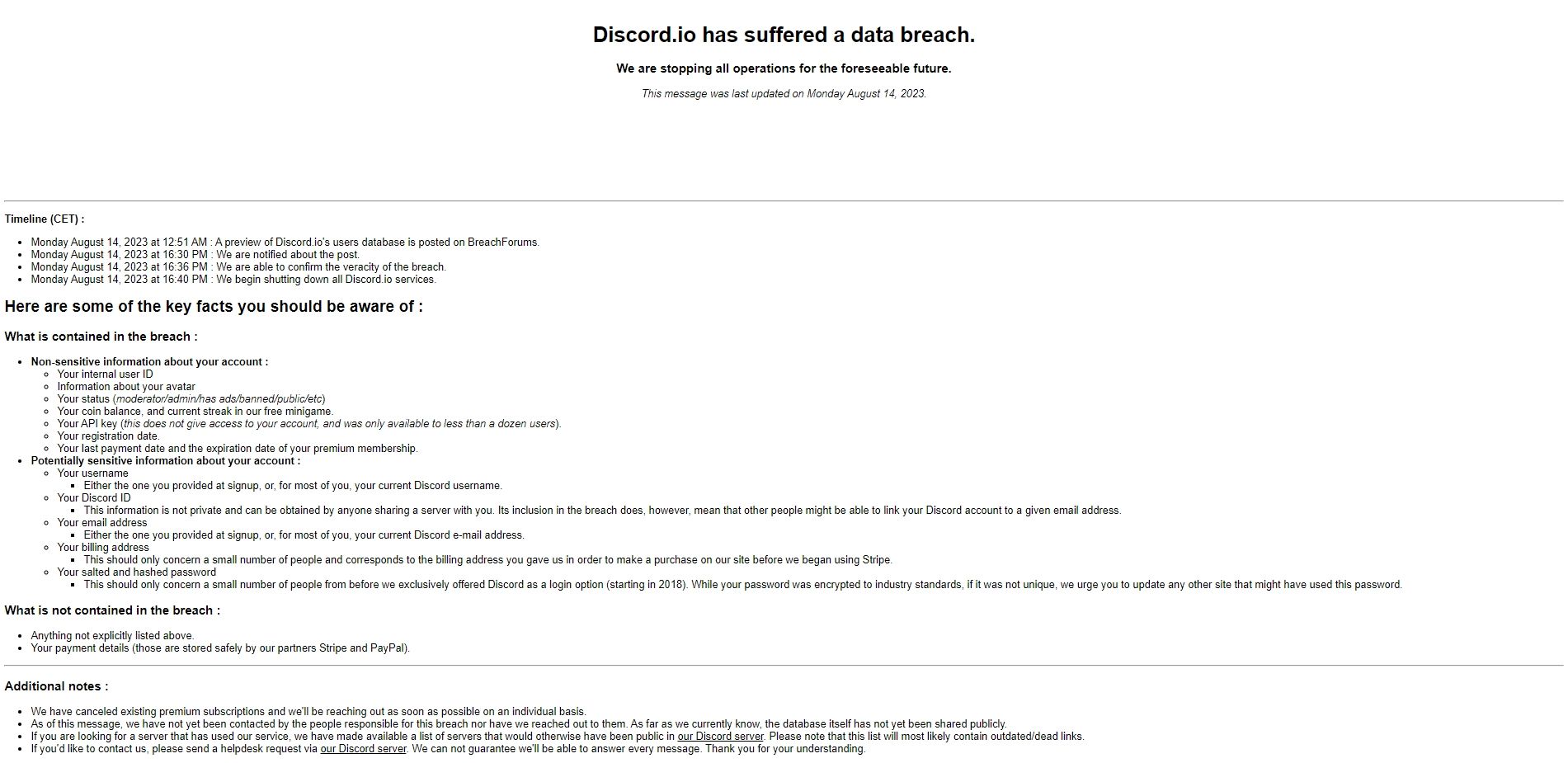
Usernames, Discord IDs, email addresses, and salted and hashed passwords have all been exposed in the database, which is concerning at first glance. The fact that passwords are hashed may seem like a little consolation, but the threat of decryption looms big, emphasizing the urgent need for users to bolster their defenses. For this reason, Discord.io has recommended users reset and update their passwords.
Furthermore, Discord.io insists that this incident did not compromise or reveal any financial information. Discord.io, however, has taken dramatic action in reaction, even if the full impact of this breach is still being determined. The service, which was already treading water, has made the difficult decision to halt its operations in the “foreseeable future.”
Maximus data breach confirmed, 11 million people at risk
A notification describing the seriousness of the breach is currently shown to visitors to Discord.io. In an effort to be transparent, the firm has listed the data fields that were hacked. The website confirmed the Discord.io data breach, and here is the official page that welcomes users:
Akrihah interview on Discord.io
After the attack, Hack Read managed to reach Akhirah, and they asked the hacker a couple of questions. When asked how they did the Discord.io data breach, Akhirah said that they don’t like Discord and its audience. Akhirah is also open to discussing with the website’s management, and they haven’t sold any information on the internet so far.
First I have to say I hate Discord and its audience, I think most of them are paedophiles, I put the data on the market to sell but I’m not sure about it, and I haven’t sold it to anyone yet, but there are so many demands, I want to talk to the management of discord.io and agree on some issues. Plus, I don’t have access to payment-related data, just stuff I’ve shared an example of.
Akhirah
Bleeping Computer also had a chance to ask the hacker why the attack occurred. Akhirah said, “It’s not just about money, some of the servers they overlook I am talking about pedophilia and similar things, they should blacklist them and not allow them.”

What is Discord.io?
Discord.io, a third-party tool that enables server operators to design unique invites to their channels, is not the official Discord website. The service’s Discord server, which has more than 14,000 users, was where the majority of the community was developed.
What is Discord.io that everybody is talking about?
What to do now?
All members should act as though their data would be misused, even though the hacker claims they haven’t sold the database. Since the passwords in this incident were scrambled using bcrypt, cracking them would need a lot of gear.
However, since they might be used in targeted phishing operations to gain more private information, email addresses can be important to other threat actors. As a result, if you are a Discord.io user, you should be on the watch for odd emails containing links to pages where you must enter your password or other details.
Inside the alarming PSNI data breach
Check the primary website, which ought to include information on prospective password resets or emails from the service, for any updates regarding the incident.
Featured image credit: Arget/Unsplash





