The use of malicious macros by cybercriminal groups has decreased by an astounding 66 percent since last October, according to research released by Proofpoint on July 28. This may be one of history’s biggest shifts in the email threat landscape.
The change is mostly a result of Microsoft’s decision to disable Excel XL4-specific macros and Visual Basic for Applications (VBA) in the Office suite as part of a series of policy changes that date back to the fall of 2013.
Cybercriminals use macros to hack users
Cybercriminals frequently utilize macros to trick consumers into executing malicious software after downloading a corrupted document from a phishing email.
Microsoft has effectively added further obstacles by disabling the ability to execute macros by default and requiring users to click and read more information about macros before permitting them to run.
Sherrod DeGrippo, Vice President of Research and Threat Detection at Proofpoint, says Microsoft’s actions yield results. In October 2021, the company saw fewer than 70 campaigns employing VBA macros, but by June 2022, this number had decreased to slightly more than 21.
“Threat actors moving away from directly distributing macro-based email attachments represents a significant change in the threat landscape. Hackers are already adopting new tactics to deliver malware, and the increased use of files such as ISO, LNK, and RAR is expected to continue,” explained DeGrippo.
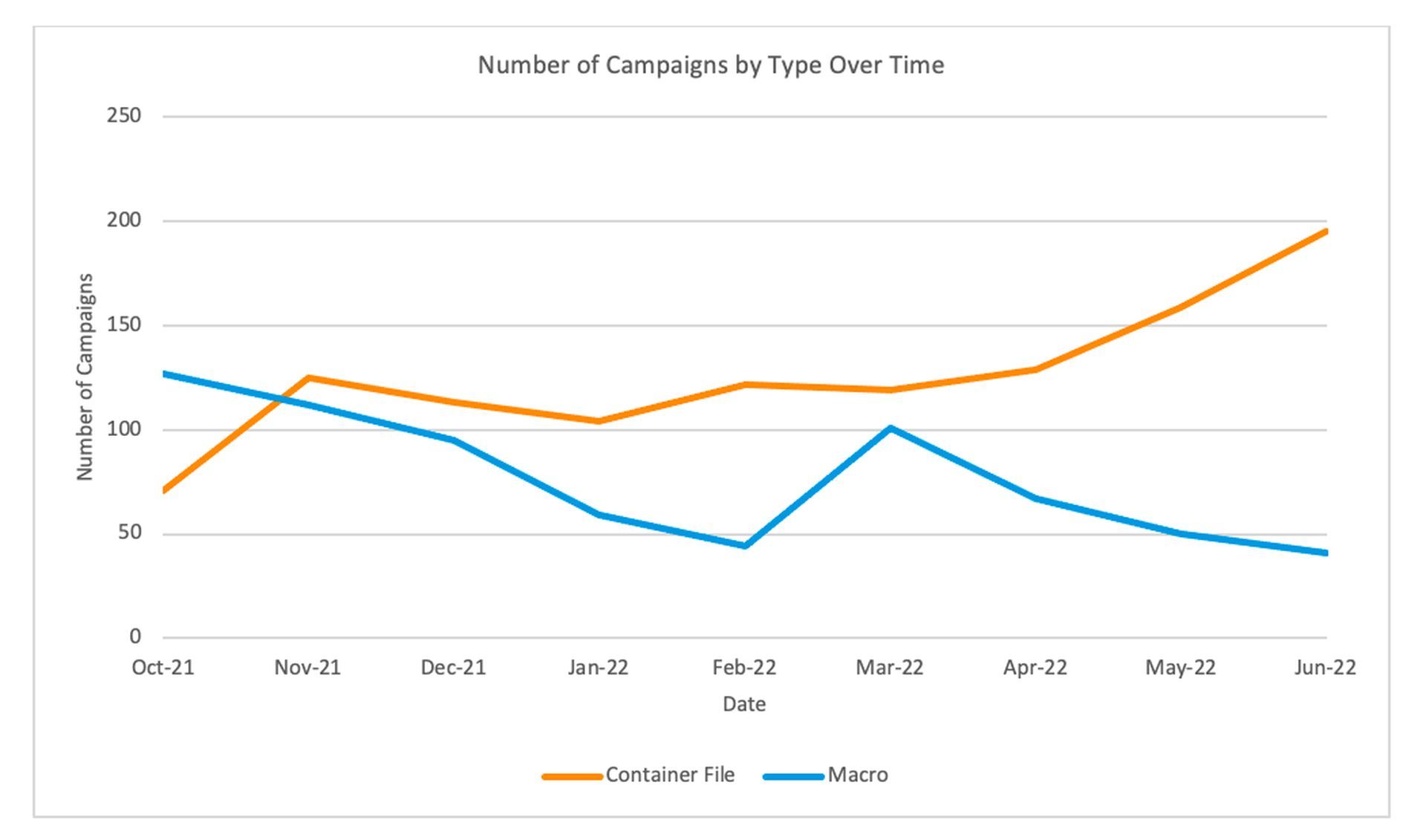
According to DeGrippo, threat actors are reportedly turning away from documents with macro functionality in droves and are instead increasingly using other vectors to infiltrate unknowing people. Proofpoint anticipated that something similar might occur.
Phishing email detection tool that helps users avoid cyber-attacks
For instance, attachments with container files like ISO and RAR are becoming more and more popular. Over the same time period, their combined volumes increased by over 200 percent, rising from roughly 70 monitored campaigns in October of last year to nearly 200 in June of this year.
This way, hackers can avoid the Mark of the Web (MOTW) measure, which Microsoft uses to prevent VBA macros from running.
Although ISO and RAR files have the MOTW attribute (because they were still downloaded from the Internet), the documents they contain won’t run dangerous code when unpacked; instead, the user must enable macros. They will compromise because their system won’t recognize the difference.
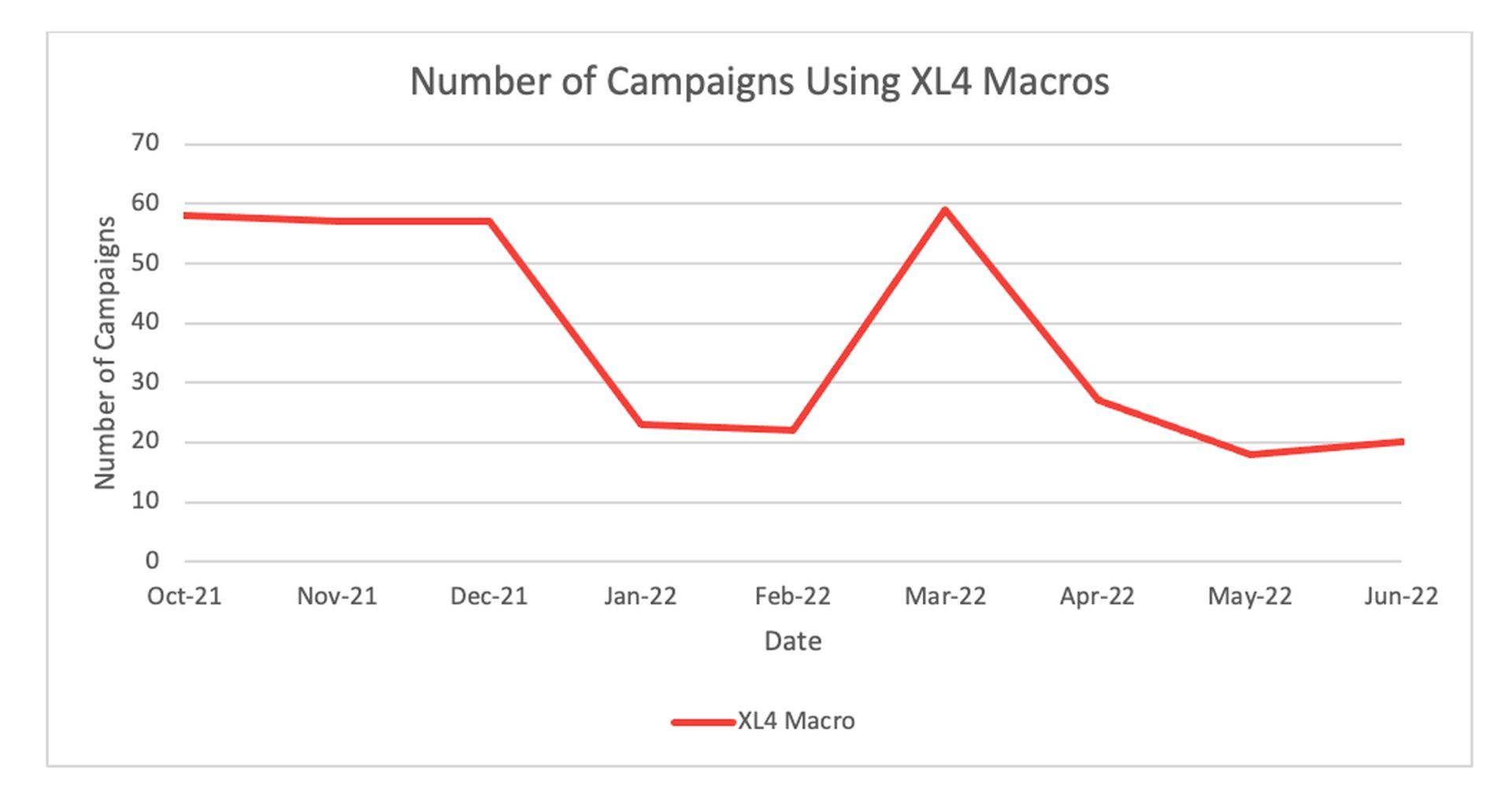
Other executable files, such as Windows Shortcut (LNK) files and Dynamic Link Libraries (DLLs), can also be distributed directly by cybercriminals using container files. Last October, Proofpoint only noticed a handful of LNK campaigns, but by June, that number had risen to slightly over 70.
Additionally, there is a little but statistically significant rise in the use of HTML files for these functions.
In the end, malware, ransomware, intelligence, and data theft are all possible, according to Proofpoint, if the target system is compromised and malicious payloads are executed on it.
The modifications were appreciated, but they weren’t easy to implement. Microsoft discreetly changed the default blocking strategy at the beginning of July 2022, citing user complaints.
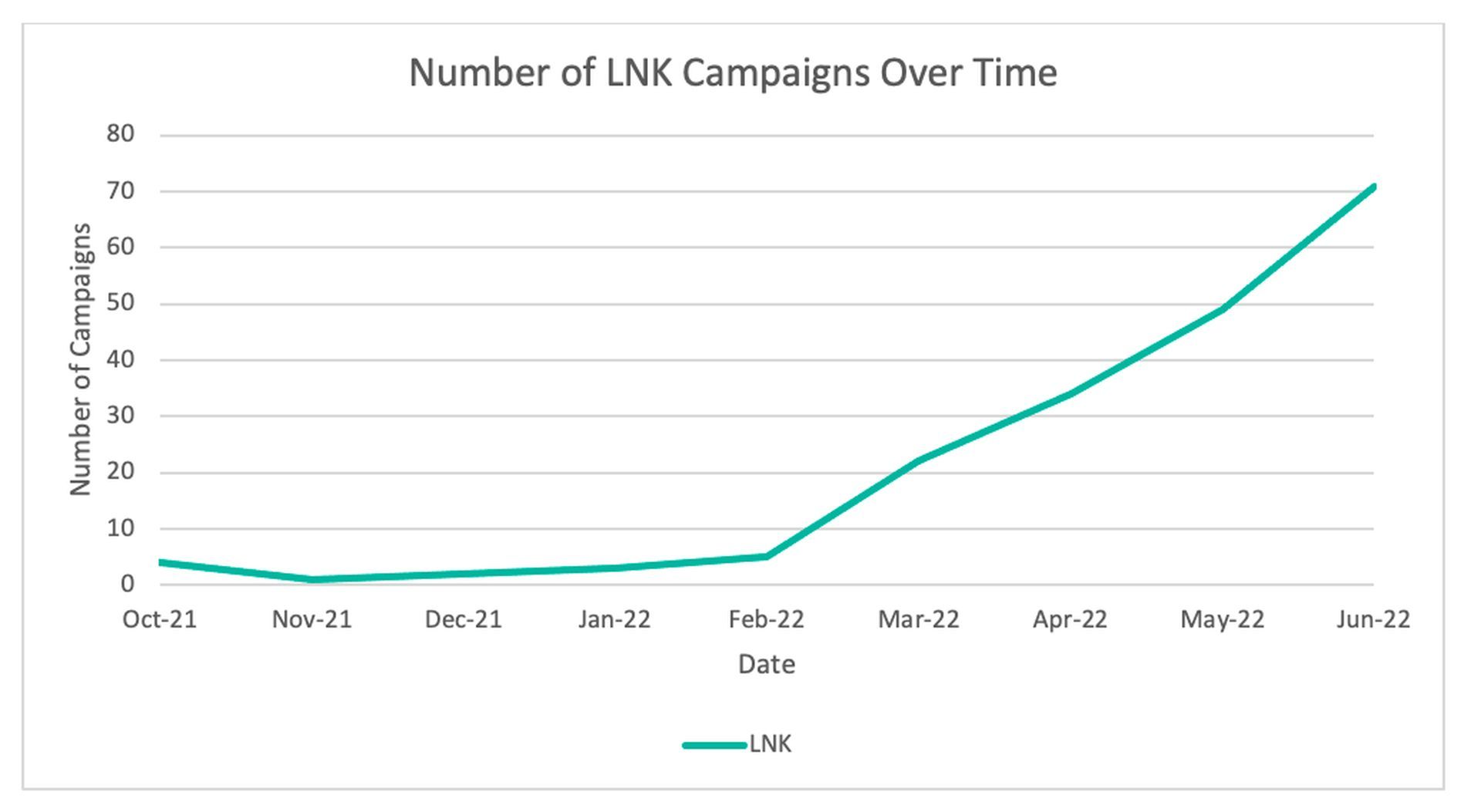
While Microsoft made certain policy adjustments, this action was reversed; nonetheless, default blocking has now been restored.
Microsoft declined to comment on the precise nature of the negative feedback. Still, Product Manager Kelly Eickmeier stated, “We’ve made updates to both our end-user documentation and IT admin documentation to clarify your options for different scenarios. For example, when you have files in SharePoint or on a network share,” in a note outlining the reinstatement of the policy.
Employees ignore cybersecurity training sessions
DeGrippo and a number of her colleagues had previously expressed their dismay at the policy suspension amid widespread concern in the security community at large.
In the past, DeGrippo and a few of her coworkers had expressed their shock at the policy suspension despite widespread anxiety in the security industry as a whole.
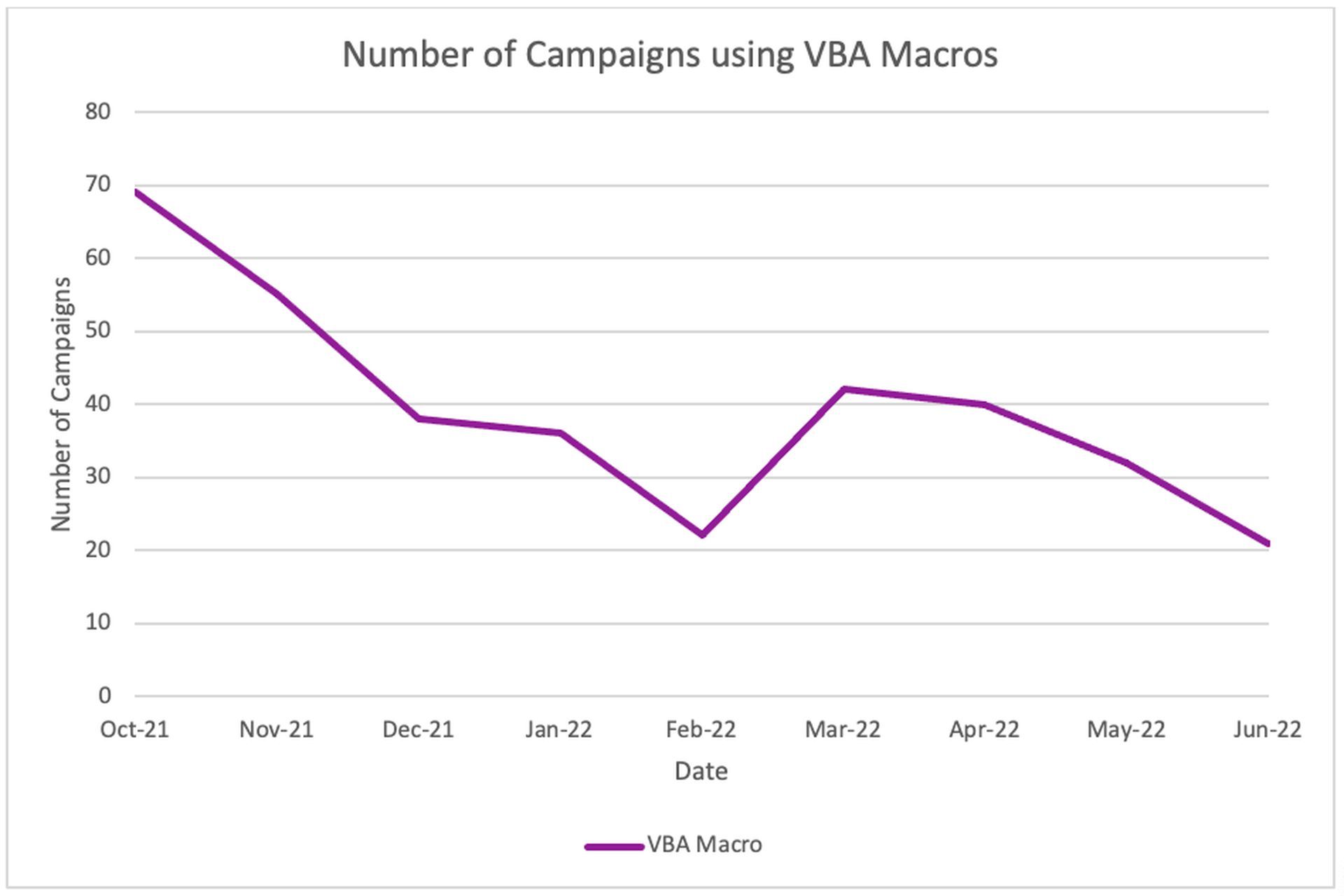
But it doesn’t seem like there is any proof that the initial and subsequent reverses had any effect on the trend away from macros. DeGrippo provided the following justification: “Threat actors had started investigating and implementing macro-blocking bypasses when the announcements happened, so they were already ahead of any real implementation.”
“The confusion over when Microsoft would continue to block by default was relatively short-lived and did not have a noticeable impact on the threat landscape. We will continue to see increased adoption of the tactics described in the blog as macro blocking becomes more widespread,” she added.





