A multi-country botnet using over 100,000 IP addresses began targeting Remote Desktop Protocol services in the United States on October 8. Researchers at threat monitoring platform GreyNoise are tracking this large-scale campaign, which they believe is launched by the extensive botnet.
Remote Desktop Protocol (RDP) is a network protocol that enables remote connection to and control of Windows systems. It is commonly utilized by administrators, helpdesk staff, and remote workers. Attackers frequently target the protocol by scanning for open RDP ports, attempting brute-force logins, exploiting vulnerabilities, or performing timing attacks to gain unauthorized access.
For this campaign, GreyNoise researchers found the botnet employs two specific RDP-related attack techniques to enumerate user accounts. The methods include:
- RD Web Access timing attacks: These probes measure response-time differences during anonymous authentication flows on RD Web Access endpoints to infer valid usernames.
- RDP web client login enumeration: This technique interacts with the RDP Web Client login flow, observing differences in server behavior and responses to identify user accounts.
GreyNoise first detected the campaign after observing an unusual traffic spike from Brazil. Similar activity was then registered from Argentina, Iran, China, Mexico, Russia, South Africa, and Ecuador. According to the company, the full list of countries with compromised devices participating in the botnet now exceeds 100.
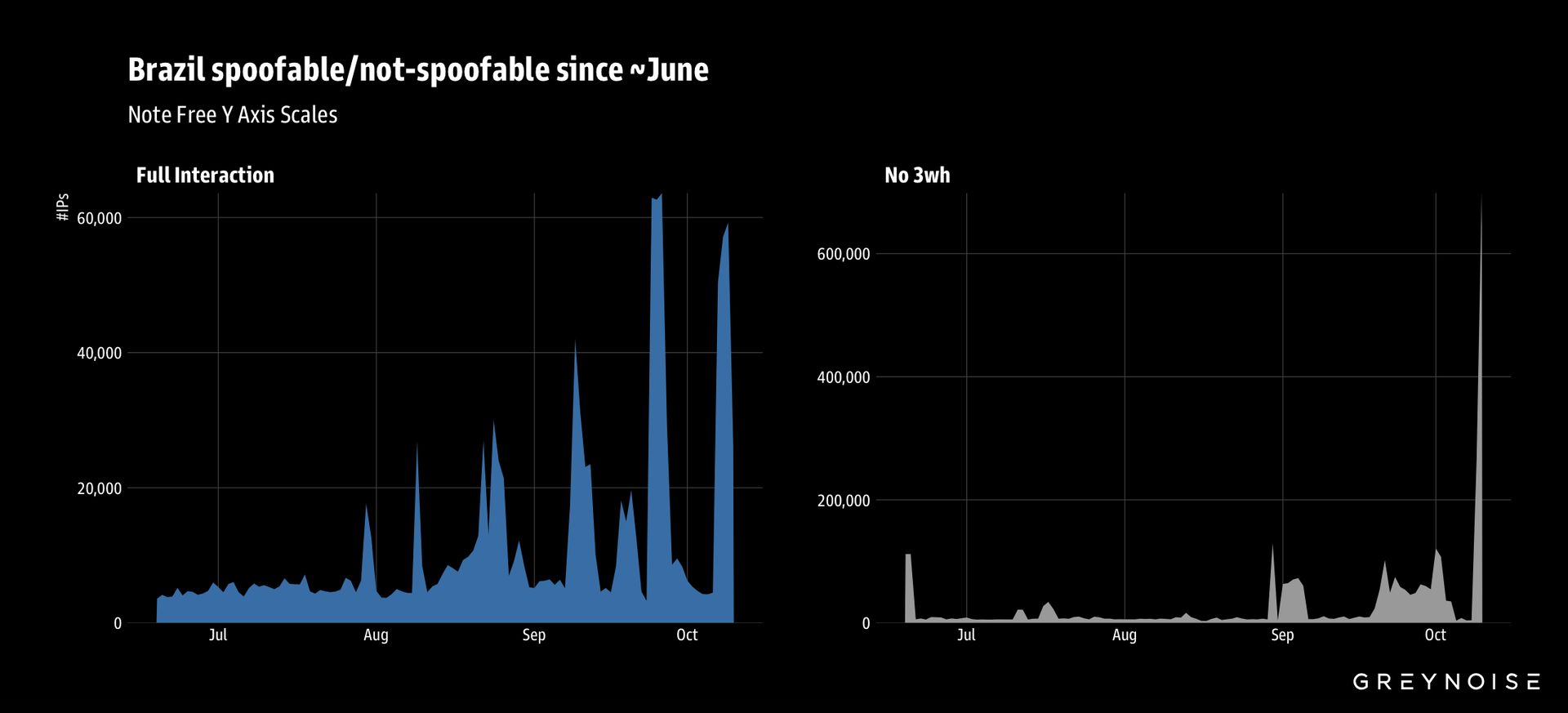
A technical analysis revealed that nearly all attacking IP addresses share a common TCP fingerprint. Although researchers noted variations in the Maximum Segment Size, they believe these differences are due to the various clusters of compromised machines that constitute the botnet infrastructure.
To defend against this activity, system administrators are recommended to block the IP addresses launching the attacks and to review system logs for suspicious RDP probing. As a general security best practice, RDP services should not be exposed directly to the public internet. Adding a VPN and multi-factor authentication (MFA) provides an additional layer of protection.





