A new cyber threat known as DoubleClickjacking has emerged, exploiting a two-click sequence to bypass existing web security protections and potentially leading to account takeovers across major websites. Discovered by security researcher Paulos Yibelo, this sophisticated attack manipulates the timing between clicks, presenting significant risks to users.
New cyber threat DoubleClickjacking exploits clicks for account takeovers
DoubleClickjacking builds on the concept of clickjacking, which typically misleads users into unknowingly clicking on hidden or disguised buttons. Traditional defenses have been strengthened in modern browsers—such as setting cookies to “SameSite: Lax” by default—yet DoubleClickjacking circumvents these measures. The attack involves a subtle manipulation where users are tricked into double-clicking on a benign prompt. During this sequence, attackers exploit the event timing to swap the content of the parent browser window with a sensitive page, such as an OAuth authorization dialog, thus allowing malicious actions to be authorized with the second click.
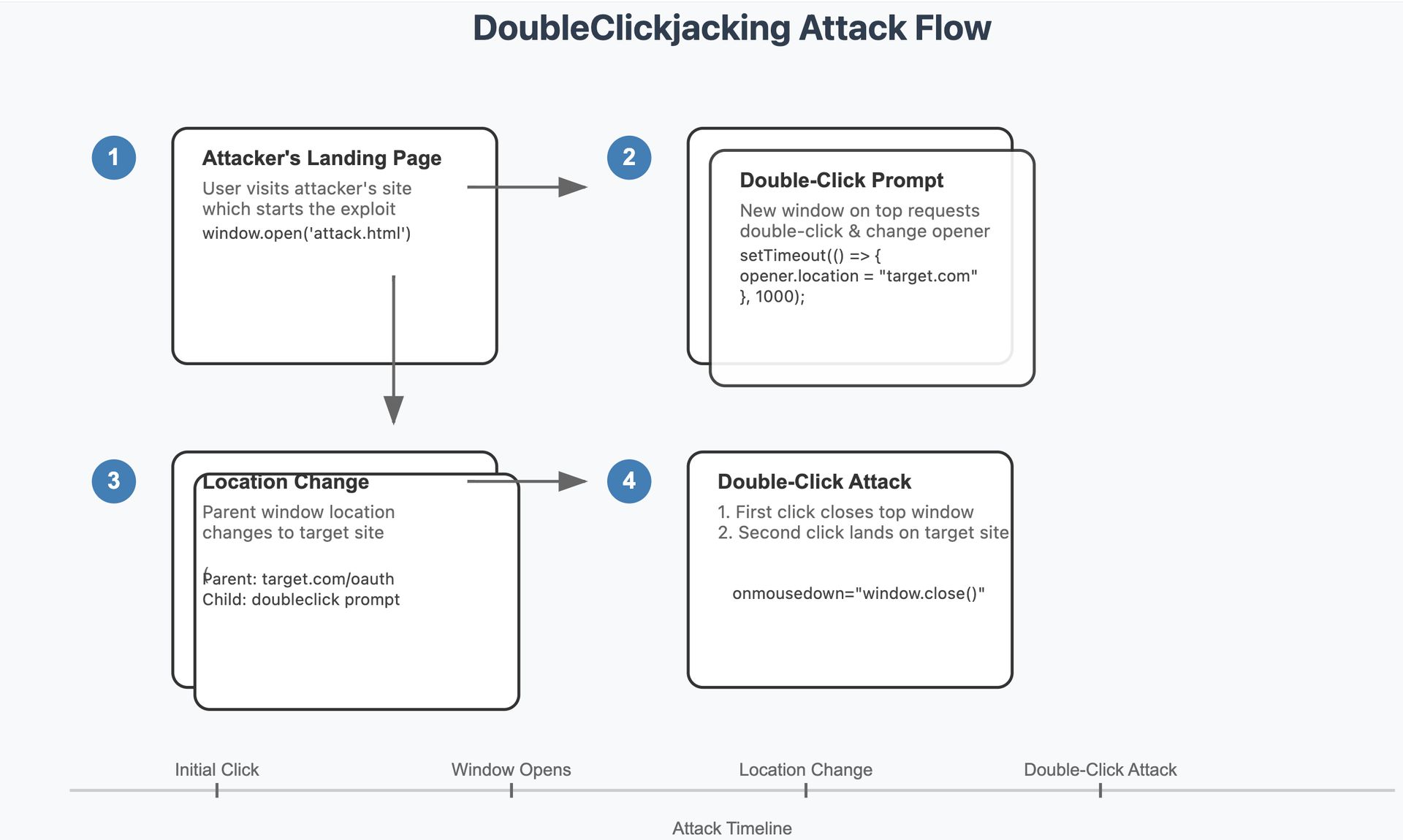
The process starts when an unsuspecting user visits an attacker’s site, led to believe they must double-click to verify they are not a robot. Upon clicking, the new window opens, and as the user prepares to double-click, the parent site’s content is altered. The closing of the top window on the first click and the landing on a sensitive element with the second click permits attackers to gain unauthorized access to accounts.
Affected websites are at risk of account takeovers, unauthorized application access with extensive data privileges, and alterations to critical account settings or financial transactions. Major websites relying on OAuth, including Salesforce, Slack, and Shopify, have been highlighted as vulnerable to this attack.
While traditional defenses like X-Frame-Options headers and Content Security Policies are designed to thwart clickjacking, they fail against DoubleClickjacking. The exploit requires minimal user interaction—a mere double-click—making it particularly deceptive. Furthermore, it extends beyond websites, also threatening browser extensions like crypto wallets or VPNs, potentially allowing attackers to disable security features or authorize financial transactions.
To mitigate this risk, several strategies are recommended. Developers can implement client-side protections, such as disabling sensitive buttons by default until intentional user action is detected. For instance, a JavaScript solution can keep buttons disabled until mouse movement or key presses occur. Long-term, browser vendors are urged to introduce new standards similar to X-Frame-Options, including a Double-Click-Protection HTTP header, to guard against this exploit.
Featured image credit: Kerem Gülen/Midjourney