Cloud services are now the foundation for most organizations’ operations. From customer apps to backend systems, everything runs in the cloud. This shift has created new challenges for security teams who must protect a growing number of systems, users, and data flows.
Traditional security methods struggle in this environment. Tools built for static infrastructure can’t keep up with cloud environments that change constantly.
This rise in concern isn’t surprising. Teams collect terabytes of logs and metrics, but often lack the tools to turn that information into meaningful insights.
Companies spend more on infrastructure, yet can’t easily track which services are secure, who has access, or where misconfigurations are hiding. Without scalable security practices, cloud investments can introduce new risks instead of reducing them.
Security challenges in distributed systems
Today’s cloud systems are distributed by design. Organizations use multiple accounts, regions, and providers. Applications are made up of microservices. Infrastructure changes are frequent and often automated. All of this creates more opportunities for errors, inconsistencies, and vulnerabilities.
A global study by the Cloud Security Alliance found that 65% of organizations rank cloud security as a top priority, and 72% believe it will become even more critical in the near future.
When something goes wrong in a distributed system, it’s often due to many small events that interact in unexpected ways. In June 2024, Cloudflare experienced a service slowdown caused by a combination of changes across its global edge network. Each change was small on its own, but together they caused a noticeable performance impact for users worldwide.

In a separate incident, an update from CrowdStrike in July 2024 triggered Windows system failures across many businesses running Windows. A single software issue spread rapidly and caused massive operational disruptions.
Automation for compliance
Most companies must follow some kind of compliance framework. These might require data encryption, backup retention, limited access to sensitive data, or audit logging. Managing these manually is inefficient, especially in large environments where resources are created and updated constantly.
Cloud platforms now offer ways to automate compliance. AWS Config is one example. It continuously monitors cloud resources and checks them against security policies. For instance, if a new database is created without encryption, AWS Config can detect it and send an alert or trigger a fix.
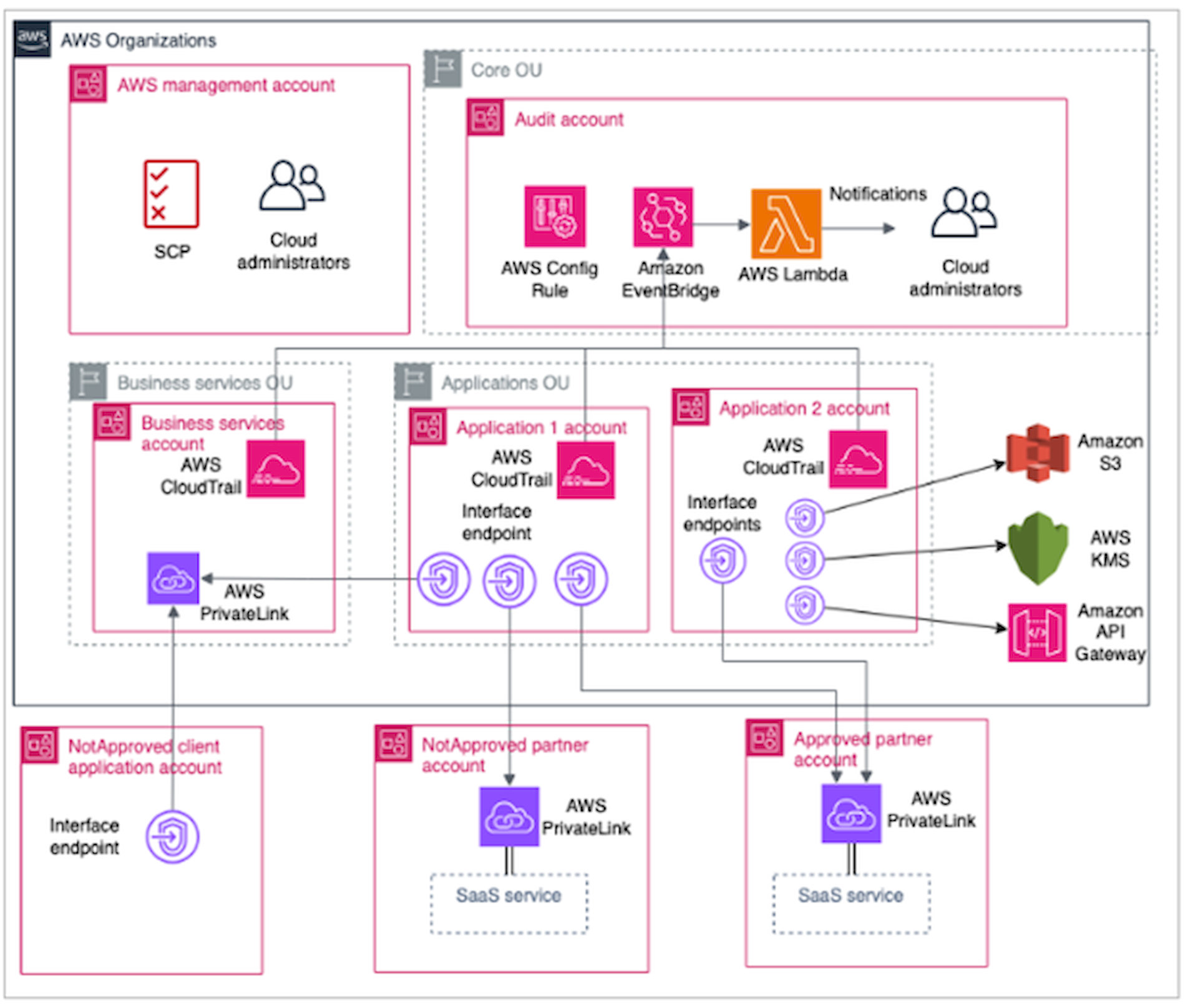
Organizations can also group multiple compliance rules into packages called conformance packs. These packs align with industry frameworks such as PCI DSS, NIST, and CIS. They help standardize enforcement across teams and environments without building everything from scratch.
Automation turns compliance from a one-time task into a continuous process. Instead of waiting for audits to find issues, teams get real-time visibility. They can correct misconfigurations immediately, keep detailed logs for reporting, and reduce the burden on security and operations teams.
Processing 3.6 billion events a week with intelligent monitoring
Cloud systems produce a constant stream of events. These include configuration changes, user logins, access requests, network updates, and system logs. In large environments, the total number of events can reach billions per week.
If an organization processes 3.6 billion events in a week, that’s over 8,000 events every second. No human team can review that amount of information manually. This is where intelligent monitoring becomes critical.
Microsoft processes more than 65 trillion signals daily, using AI and machine learning to identify patterns and detect threats.

At a smaller but still significant scale, companies can use similar approaches. They filter out low-risk data, highlight anomalies, and use automated workflows to investigate issues. Intelligent monitoring also helps reduce alert fatigue by focusing on signals that matter. Instead of drowning in data, teams receive curated insights and can respond faster to real problems.
Using serverless workflows for compliance assurance
Serverless technology allows teams to create event-driven workflows that run only when needed. This is especially useful for compliance. When a cloud resource violates a policy, a serverless function can trigger immediately to take action.
For example, if a storage bucket is created without proper encryption or access controls, a serverless workflow can automatically lock it down, tag it for review, and log the event for audit. These workflows are built using tools like AWS Config, Step Functions, and Lambda.
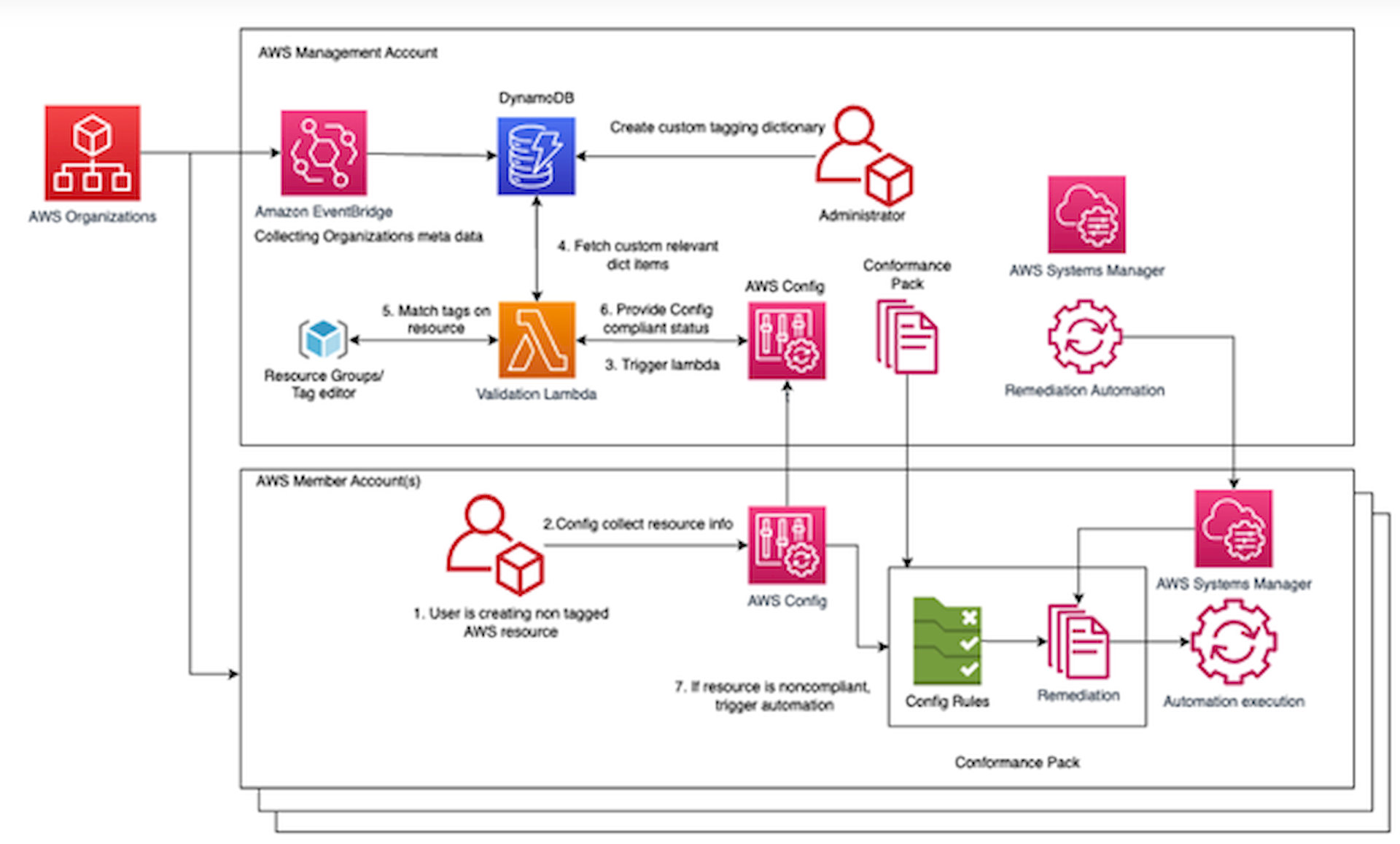
Since serverless services only run when triggered, they are cost-effective and scale easily. They allow security and compliance policies to operate as real-time systems rather than background processes. Organizations can standardize enforcement across regions, accounts, and teams without constant manual intervention.
Serverless workflows also provide consistent responses. The same issue always gets the same fix. This reduces variability, improves audit readiness, and allows teams to focus on higher-value work.
AI in security operations: How generative AI reshapes detection, response, and prevention
Security teams often work under pressure. They need to find issues quickly, understand what caused them, and decide how to respond. This is hard to do in cloud environments where services are connected, logs are scattered, and alerts are constant.
Generative AI is helping by summarizing data, suggesting next steps, and turning complex logs into plain-language insights. Amazon Bedrock provides access to large language models that teams can use to answer questions like, “Why did our cloud costs spike last week?” or “What changed before this outage?”

AI also assists with detection. Fortinet’s research shows that AI tools are helping teams reduce noise, prioritize high-risk alerts, and accelerate investigations.
These tools do not replace analysts, but they extend what analysts can do. Instead of reading hundreds of logs, a security engineer can ask the AI for a summary. Instead of manually piecing together an attack path, the AI can propose likely connections. This makes security operations faster, more accurate, and more scalable.
Engineering leadership for secure innovation
Engineering leadership plays a critical role in how organizations handle cloud security. It’s not enough to buy the right tools or hire more people. Leaders must define clear goals, set expectations, and create a culture that supports secure and reliable operations.
Successful teams measure outcomes. They track metrics like time to recover from incidents, the number of policy violations caught before deployment, and the cost of maintaining secure systems. These indicators help teams understand whether they’re improving and where they need to invest.
Google’s Site Reliability Engineering model provides useful guidance. It encourages shared responsibility between development and operations, regular learning from incidents, and a focus on building resilient systems.

Leadership should also ensure that developers have the tools and knowledge to build securely from the start. This includes integrating security checks into development pipelines, providing clear guidelines, and making it easy to do the right thing.
When security is part of daily work instead of a separate step, teams move faster and make fewer mistakes.
The new frontier is trust-driven cloud systems
Cloud systems are no longer just technical platforms. They are the foundation for customer relationships, regulatory obligations, and internal operations. As these systems grow, so does the need for trust.
Trust means knowing your infrastructure is secure, your data is protected, and your operations are compliant. It also means being able to prove these things with real evidence at any moment.
Building trust at scale requires continuous monitoring, automated compliance, smart use of AI, and leadership that supports secure practices. Organizations that invest in these areas can move faster, avoid costly incidents, and earn confidence from their customers, partners, and regulators.
Security is no longer just about avoiding risk; it’s also about mitigating it. It’s about enabling progress. With the right design, cloud security becomes a tool for growth, not a barrier to it.





