Malicious VSCode extensions pose a significant threat to users of the popular coding tool.
Researchers recently uncovered that these harmful add-ons have infiltrated the VSCode Marketplace, putting numerous organizations at risk.
What’s the deal with malicious VSCode extensions?
A team of researchers from Israel examined the security measures of the Visual Studio Code (VSCode) marketplace and succeeded in “infecting” more than 100 organizations by embedding malicious code into a modified version of the widely-used ‘Dracula Official‘ theme. Their investigation into the VSCode Marketplace revealed the presence of thousands of extensions with millions of downloads.
VSCode, a source code editor developed by Microsoft, is extensively utilized by professional software developers globally. Microsoft also oversees an extension market for this integrated development environment (IDE), known as the Visual Studio Code Marketplace. This marketplace provides various add-ons that enhance the application’s functionality and customization.
One letter makes all the difference
In their recent experiment, researchers Amit Assaraf, Itay Kruk, and Idan Dardikman developed an extension designed to typosquat the popular ‘Dracula Official’ theme, a favorite color scheme with over 7 million installs on the VSCode Marketplace. Due to its appealing dark mode and high-contrast color palette, ‘Dracula’ is widely used by developers to reduce eye strain during prolonged coding sessions.
The counterfeit extension, named ‘Darcula,’ was meticulously crafted, and the researchers even registered the domain ‘darculatheme.com.’ This domain was utilized to establish a verified publisher status on the VSCode Marketplace, thereby lending authenticity to the fake extension.
Their version of the extension contained the legitimate code from the actual Dracula theme but with an additional script designed to gather system information such as the hostname, number of installed extensions, device’s domain name, and the operating system platform. This data was then transmitted to a remote server through an HTTPS POST request.
The researchers pointed out that the malicious code embedded within the extension evades detection by endpoint detection and response (EDR) tools. This evasion occurs because VSCode, given its role as a development and testing environment, is often treated leniently by security tools.
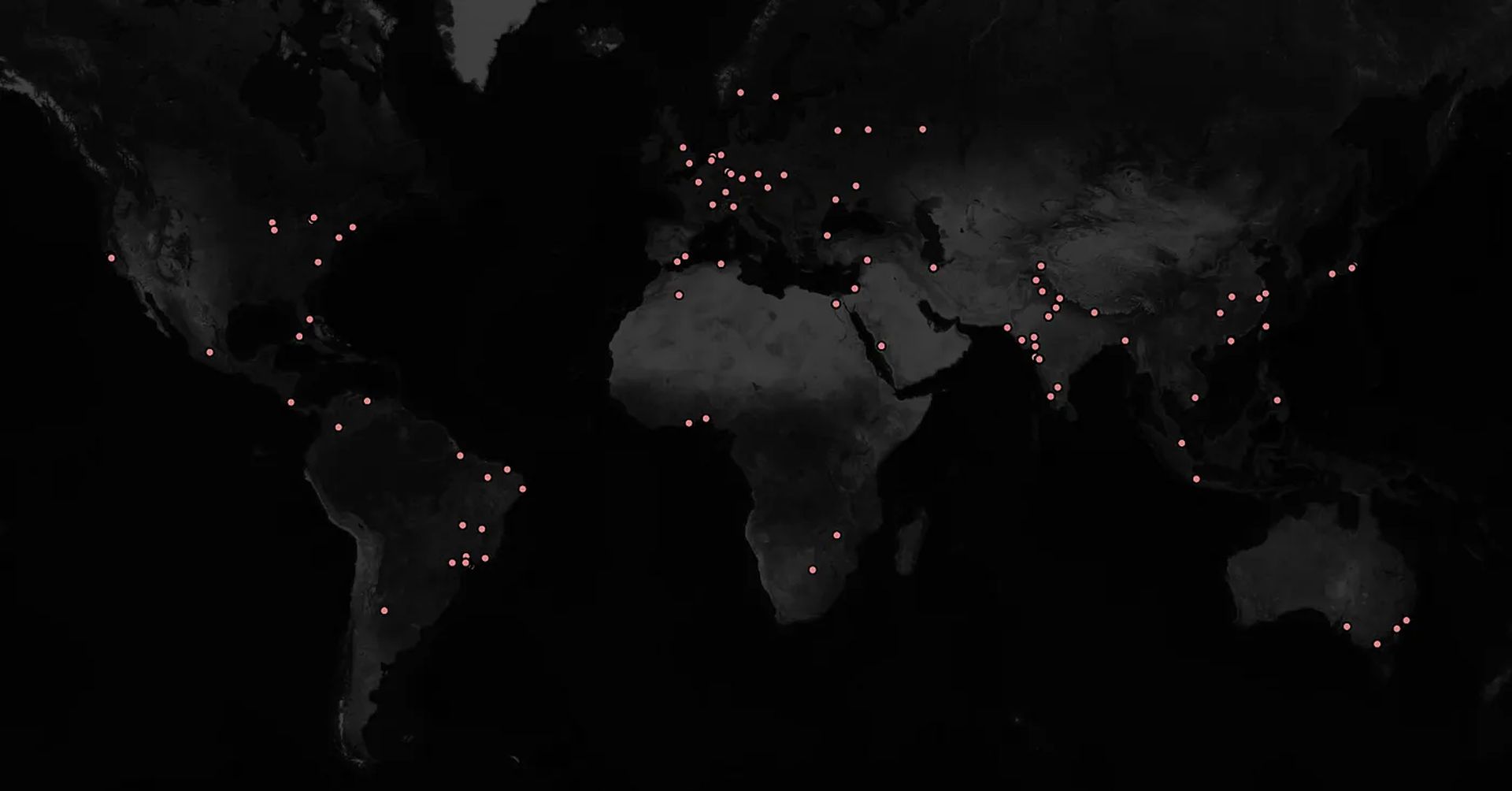
“Unfortunately, traditional endpoint security tools (EDRs) do not detect this activity (as we’ve demonstrated examples of RCE for select organizations during the responsible disclosure process). VSCode is built to read lots of files and execute many commands and create child processes, thus EDRs cannot understand if the activity from VSCode is legit developer activity or a malicious extension,” stated Amit Assaraf.
The Malicious VSCode extensions quickly gained traction and was inadvertently installed by several high-value targets, including a publicly listed company with a market capitalization of $483 billion, major security firms, and a national justice court network. The researchers chose not to disclose the identities of the affected organizations.
Given that the experiment was not intended to cause harm, the researchers only collected identifying information and included a disclosure in the extension’s Read Me, license, and code.
Status of VSCode Marketplace
Following their successful experiment, the researchers decided to delve deeper into the threat landscape of the VSCode Marketplace. Utilizing a custom tool they developed, named ‘ExtensionTotal,’ they sought to identify high-risk extensions, unpack them, and examine suspicious code snippets.
This investigation revealed the following:
- 1,283 extensions containing known malicious code, totaling 229 million installs.
- 8,161 malicious VSCode extensions communicating with hardcoded IP addresses.
- 1,452 extensions executing unknown executables.
- 2,304 extensions utilizing another publisher’s GitHub repository, suggesting they are copycats.
An example of code found in a malicious VScode extension includes one that opens a reverse shell to a cybercriminal’s server.

The researchers highlighted that Microsoft’s insufficient controls and code review mechanisms on the VSCode Marketplace facilitate rampant abuse of the platform. This issue is exacerbated as the platform’s usage continues to grow.
“As you can tell by the numbers, there are plethora of extensions that pose risks to organizations on the Visual Studio Code marketplace,” the researchers cautioned. “VSCode extensions are an abused and exposed attack vertical, with zero visibility, high impact, and high risk. This issue poses a direct threat to organizations and deserves the security community’s attention.”
The Snowflake data breach is a tangled mess
All detected malicious VScode extensions were responsibly reported to Microsoft for removal. However, at the time of writing, the majority of these malicious VSCode extensions remain available for download via the VSCode Marketplace.
The researchers intend to release their ‘ExtensionTotal’ tool, along with details about its operational capabilities, next week. This tool will be made available for free to help developers scan their environments for potential threats.
Featured image credit: Markus Spiske/Unsplash





